We first added checkm8 acquisition from iOS devices in Oxygen Forensic® Detective v.12.6 in July of 2020. Not surprisingly, many things have changed since then. That being the case, we updated our tool several times over the last few months to remain industry leaders in mobile forensics and provide investigators with the best solution on the market.
According to Wikipedia, iOS 15 is the fifteenth and current major release of the iOS mobile operating system developed by Apple for its iPhone and iPod Touch lines of products. It was announced at the company’s Worldwide Developers Conference on June 7, 2021, as the successor to iOS 14, and released to the public on September 20, 2021. On February 10th, 2022 iOS version 15.3.1 containing bug fixes came out.
In Oxygen Forensic® Detective v.14.3, we have updated our checkm8 acquisition method, adding support for devices operating on iOS versions 15-15.3.1
We have successfully tested the updated method on the following devices:
- iPhone 6s
- iPhone 7
- iPhone 8
- iPhone X
However, this method is likely to work correctly on other iOS devices, such as iPhone 6S Plus, iPhone SE, iPhone 7 Plus, iPhone 8 Plus, iPad 5 Gen, iPad 6 Gen, and iPad 7 Gen with the iOS version from 15-15.3.
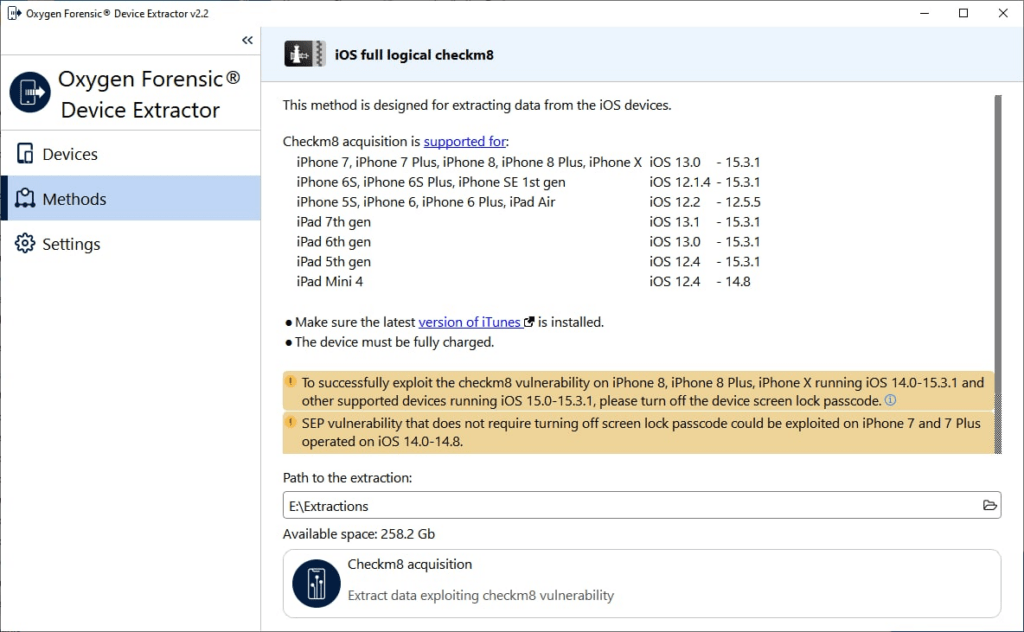
Please note that the extraction process for devices with these iOS versions differs. Previously, the device had to be put in DFU mode and then connected. With iOS versions 15-15.3.1, the device has to first be put in recovery mode for the detection of an installed iOS version. After the iOS version and device model are defined, the device has to be switched to DFU mode. The remaining steps of the data extraction process are left unchanged, as well as the data extraction process from iOS devices with iOS version lower than 15.
The reason for the need to put the device in recovery mode first lies in the security changes brought by iOS versions 15-15.3.1. Starting with iOS 15, the changes in the system partition lead to the device not operating in normal mode. In order to minimize the risk of permanently damaging the device, we had to develop a solution that does not modify any device data. Contrary to other iOS versions, in iOS 15 and higher the executable files are put in RAMDisk that loads in recovery mode. With RAMdisk loading to RAM, the system partition remains unchanged.
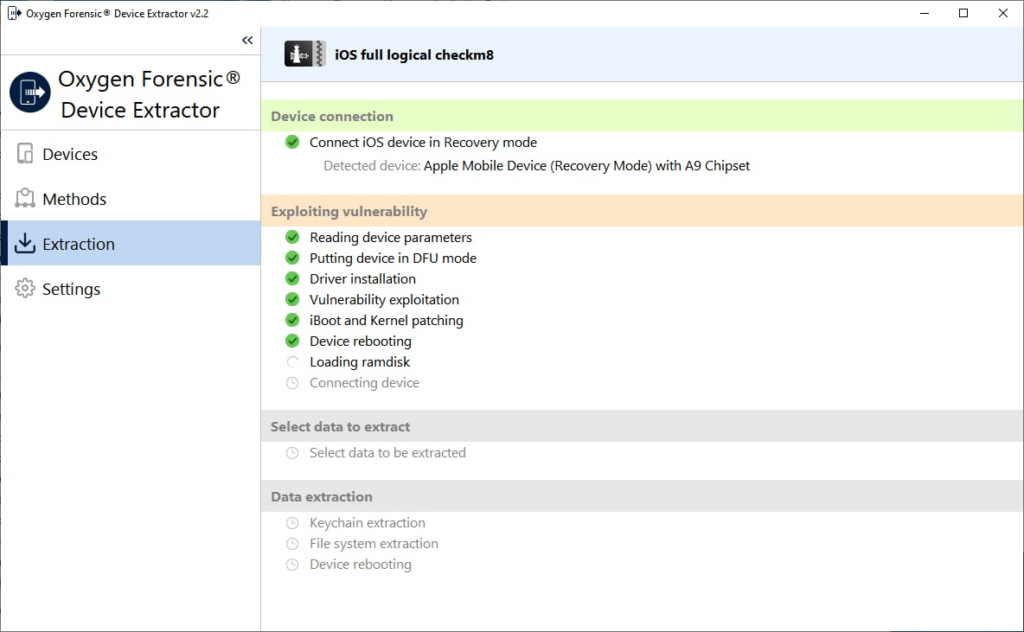
Extraction of Keychain from devices with iOS 15 and higher has been altered as well. The method used for iOS devices with their version below 15 cannot be applicable for iOS 15+ devices because the device is loaded into our own environment from RAMDisk, which bypasses the standard boot protocol. Thus, we had to implement the decryption of Keychain data directly, without using the standard phone environment.
In the updated checkm8 extraction method, we do not use the API of the operating system, but parse and decrypt all the Keychain entries on the Oxygen Forensic® Device Extractor side, using the device only to overcome the protection with hardware keys. Therefore, a new Keychain Dumper has been developed to extract Keychain records from iOS 15+ devices.
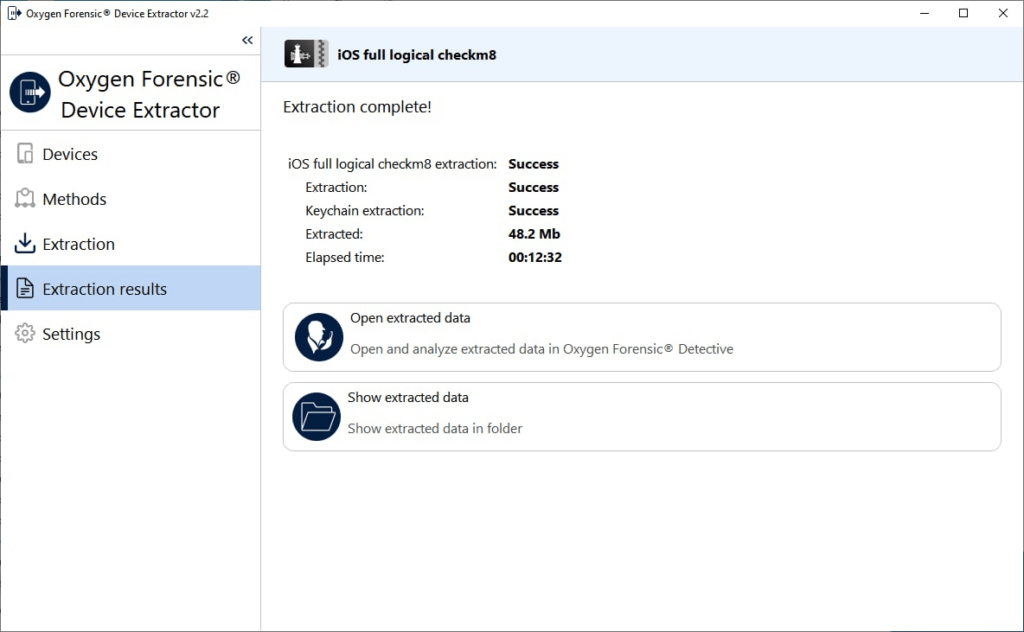
This method can be used for extracting data from newer iOS versions, since it does not alter the system device partition in any way. Device loads into our own environment, bypassing the standard boot protocol. This allows adding to RAMDisk support of the higher iOS versions and new devices. We might use this method for checkm8 data extraction from all iOS devices and versions in the future, since it is more forensically sound, versatile, and easier to control.
Interested in trying our new checkm8 support capability for iOS 15 but don’t have an Oxygen Forensic® Detective license? Request a free, fully-equipped, 20-day trial by clicking here.