Brave Browser was created by Brendan Eich, one of the two co-founders of Mozilla. This privacy-focused browser is based on Google’s open-source Chromium code. The Brave Browser report shows that Brave now has over 36.2 million monthly active users and over 12.5 million daily active users. In several “best secure browser ratings of 2021”, Brave Browser occupies the top position, even higher than the Tor Browser.
What makes it popular are the privacy features that are offered by default. Among them are:
- Blocking of all ads, pop-ups, scripts, trackers, third-party cookies, and third-party storage
- Upgrading insecure connections to HTTPS
- The possibility to open a new private window with the Tor connectivity and DuckDuckGo default search engine, means that users can easily access the Dark web that is often associated with illegal activities
These secure features can be used for both good and bad. In this blog article, we will focus on how Brave Browser data can be extracted as digital evidence from mobile devices. Please note that a mobile version of Brave browser does offer the Tor connectivity, so this topic won’t be discussed here.
Brave Browser extraction from Apple iOS devices
Oxygen Forensic® Detective offers Brave Browser data extraction via iTunes backup procedure or checkm8 method. Both methods require an Apple iOS device to be unlocked before extraction.
The evidence set includes:
- Web history
- Search history
- Bookmarks
- Downloads
- Tabs
- Top sites
- Logs
- Cache
- Cookies
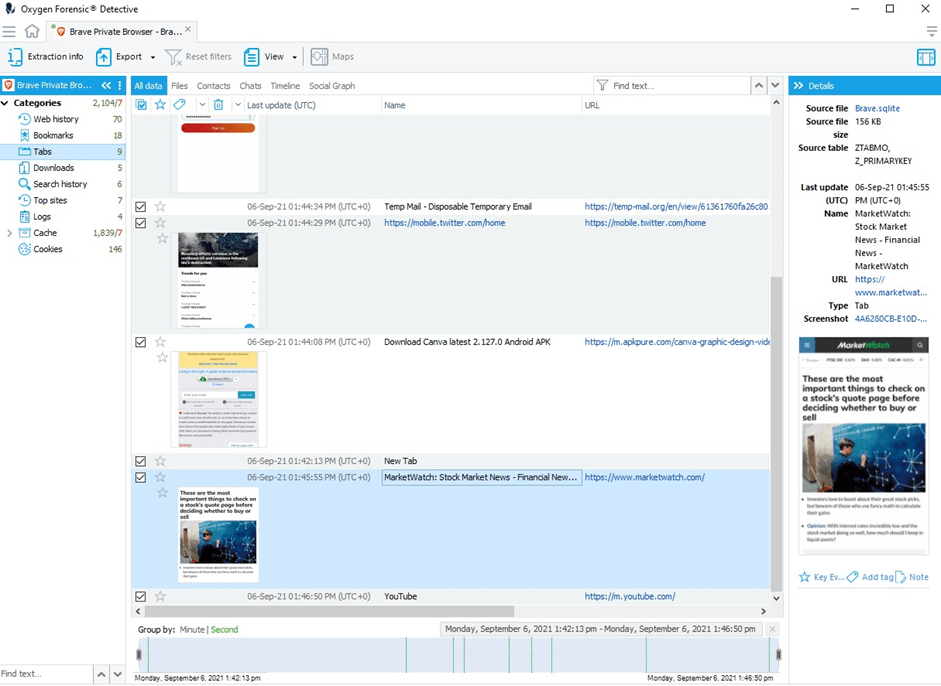
Passwords saved in the Brave Browser require decryption. Their parsing will be added in the upcoming versions of Oxygen Forensic® Detective.
Brave Browser extraction from Android devices
Brave Browser data from Android devices can be acquired by a greater variety of methods, including screen lock bypass techniques for many Samsung, Huawei, Sony, LG and other devices based on MTK, Qualcomm, and Spreadrum chipsets.
The evidence set includes the following:
- Account details
- Saved passwords
- Web history
- Search history
- Bookmarks
- Downloads
- Tabs
- Autofill data
- Top sites
- Logs
- Cache
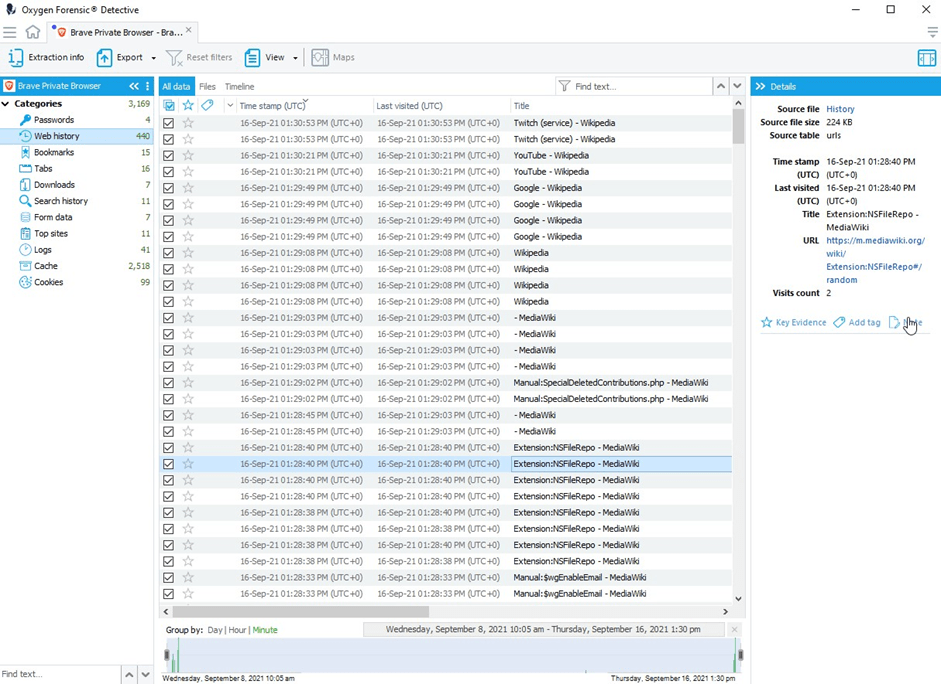
Please note: if browsing is done in private mode, no data is available for extraction.
Currently, we are working on giving investigators accessibility to collect Brave Browser data on computers using Oxygen Forensic® Detective. Once support is implemented, we will share the details with you.
If you need support for an app that is not yet covered by Oxygen Forensic® Detective, do not hesitate to submit an app support request.