Today, macOS is the primary operating system for Apple’s Mac computers. Within the desktop, laptop, and home computer market, it is the second most widely used desktop OS, after Microsoft Windows.
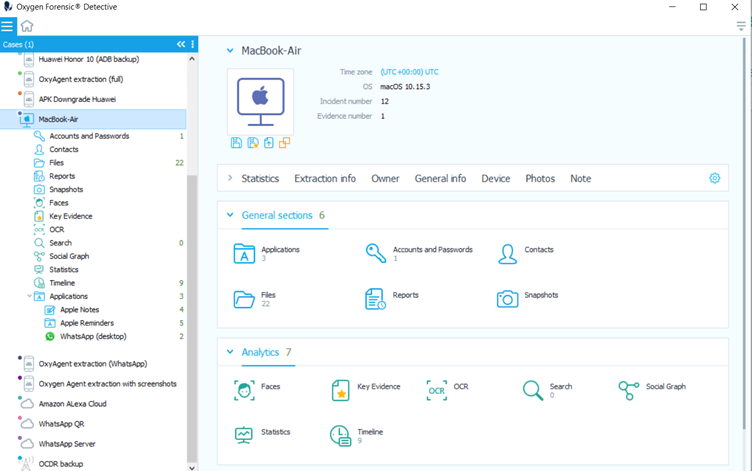
Oxygen Forensic® KeyScout, a built-in module of Oxygen Forensic® Detective , can extract data from macOS, including pre-installed Apple apps, user-installed apps, system files, and user credentials.
In this article, let’s take a look at user artifacts and credentials supported by Oxygen Forensic® KeyScout.
Extraction methods in Oxygen Forensic® Detective of macOS artifacts
There are several methods how macOS user data can be extracted in Oxygen Forensic® Detective, one being live extraction when Oxygen Forensic® KeyScout is run on the macOS computer.
Data that can be extracted (anchored list):
- Pre-installed Apple apps
- Other apps
- Credentials
The supported macOS versions are Monterey, Big Sur, Catalina, Mojave, and High Sierra.
Import and parsing of macOS images and backups:
- Time Machine backups
- E01, Ex01, raw (*.dd, *.bin, *.img, *.001, *.000, *.0000, *.0001), dmg, iso physical image
- L01, Lx01, AD1, zip, 7z, rar, tar logical image
- VirtualBox, VMware virtual machine
- vdi, vhd, vmdk virtual machine drive image
Please note that supported file systems are exFAT, HFS, HFS+, and APFS.
Pre-installed Apple apps on macOS
MacOS comes with the pre-installed Apple apps which can be synchronized with other iOS devices. These apps store different data that can be extracted with Oxygen Forensic® KeyScout.
We support the following pre-installed Apple apps:
- iCloud Drive
- Apple Calendar
- Apple Contacts
- Apple Messages
- Apple Mail
- Apple Maps
- Apple Notes
- Apple Photos
- Apple Reminders
- Safari
These apps cover the various sides of a Mac owner’s life and activities, and each of them when extracted and parsed will provide investigators with valuable information and insights.
Extraction of other apps
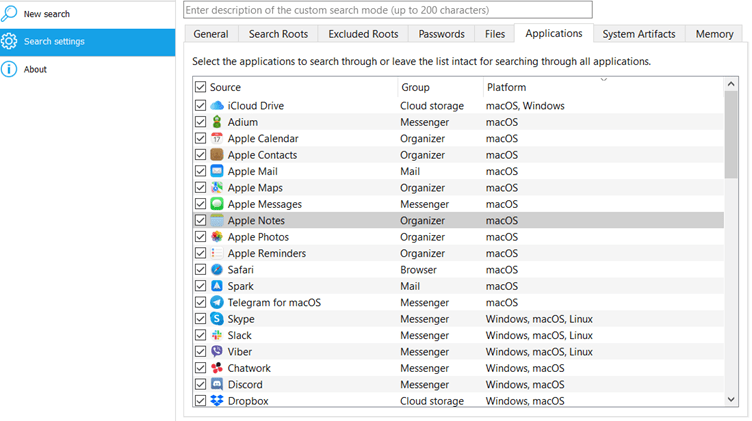
In many cases, the usage of a Mac is not limited to the pre-installed apps. Armed with Oxygen Forensic® KeyScout, investigators can extract artifacts from many popular apps.
The list includes but is not limited to:
- Messengers: Chatwork, Discord, Element, Facebook Messenger, Telegram, TamTam, Signal, Skype, Slack, Viber, WhatsApp, Zoom, and Zalo
- Mail clients: Mozilla Thunderbird and Spark
- Web browsers: Google Chrome, Opera, Microsoft Edge, and Mozilla Firefox
- Productivity: Google Drive, Google Backup, Evernote, Dropbox, Flock, OneNote, and OneDrive
We add support for new apps in every release. Investigators can always check the list of currently supported apps in the KeyScout Search settings.
Extraction of credentials
In addition, Oxygen Forensic® KeyScout can extract credentials and tokens from the majority of supported apps. Two of the most valuable tokens are WhatsApp and Telegram tokens. All the extracted credentials can be imported to Oxygen Forensic® Cloud Extractor to acquire even more evidence from the cloud.
Conclusion
Having the ability to extract user data and credentials from macOS is important, especially when 15% of the operating systems in 2021 globally were macOS.
Oxygen Forensic® KeyScout, a tool that is part of our Oxygen Forensic® Detective suite, gives investigators the ability to extract Apple app data, other app data, and credentials for macOS.
Want to try Oxygen Forensic® KeyScout? Contact us for a free trial license.