MediaTek Inc. is one of the largest smartphone chip makers in the world. At Oxygen Forensics we have implemented data extraction from Android devices based on MTK chipsets in Oxygen Forensic® Detective.
This type of extraction method is based on a low-level proprietary protocol which was designed for firmware updates and repair of MTK-based devices, allowing data extraction from password-locked devices. The majority of MTK chipsets is currently supported in Oxygen Forensic® Detective.
Table of contents
- Supported extraction methods of MediaTek devices in Oxygen Forensic® Detective
- Step-by-step: MTK Android data extraction
- Common Questions
Supported extraction methods of MediaTek devices in Oxygen Forensic® Detective
How to start
First, the device has to be put in preloader mode or BootROM (ROM) mode. These modes allow users to exchange with an MTK device via proprietary protocol.
To put the device in preloader mode, turn off the device and connect it via USB. A virtual MediaTek COM port will be exposed in the system for one second. If nothing is done during this period, the device will switch back to charging mode. However, if the handshake procedure is initiated during this time, users can continue to communicate with the MediaTek device using the special protocol.
On some devices, investigators will need to press one or both volume buttons on the turned off device and then connect the device via USB in order to enter the special mode. Only after that, the device will switch to preloader or BROM mode.
For optimal work in this mode, we recommend to install the driver included into the product package. If MTK driver is installed correctly, the extraction process will continue. Otherwise, you will have to reinstall the driver in the system or find the correct driver for this device and repeat the process.
Some devices do not work with the standard driver and require a custom driver from the manufacturer.
In preloader or BROM mode, basic information about the hardware of the MTK device under examination can be obtained.
In order to read the memory image, a special loader (DA-file) is loaded into RAM, which automatically puts the MTK device into Download Agent (DA) mode. This process does not modify the device’s firmware and therefore is safe for its operation and data storage preservation.
DA mode provides a high-level API of interaction with the device and supports commands that can be used to read device physical image. The software uses the universal DA loader. But some devices require a vendor-signed DA file to operate. For such devices to be supported in Oxygen Forensic® Detective, upload the corresponding third-party DA file into the software.
Oxygen Forensic® Detective also uses the DAA disabling technique, which allows to bypass the DA file signature check and use the universal DA file. DAA disabling is implemented via a vulnerability in BROM. During exploitation of this vulnerability, all processes are run in RAM. Therefore, this operation is safe, since the device returns to its original state after reboot.
The process in general:
- Set connection parameters – select DA file or disable DAA and use universal DA file to connect.
- Connect device in MTK mode – information about the chipset will be available at connection.
- Extract the physical image.
- Check whether the image is encrypted.
- Identify the encryption type.
- If hardware key encryption is used and the chipset is vulnerable, extract the hardware key.
- Enter screen lock password or run password brute force (if the password is set).
- The software generates a decryption key using the hardware key and the password, and then decrypts the user data.
User data encryption
Encryption of user data is enabled on Android devices by default and cannot be disabled. Starting with Android 10, file-based encryption (FBE) is used for data encryption. On earlier Android versions, full disk encryption (FDE) was used. Encryption process uses the hardware key, if the chipset supports that.
If MTK device memory is encrypted, the contents of the extracted physical image is encrypted as well. In order to decrypt it, we need to know the hardware key and lock screen password (if it was set), as well as the decryption algorithm. A part of the algorithm is common for all Android devices, but the other part is implemented within the Trusted Execution Environment (TEE) and varies for different TEE OSs.
MTK devices utilize several different TEE systems such as Kinibi, Trusty, Microtrust, T6, RSEE, etc. due to the abundance of vendors releasing their devices on MTK chipsets. The TEE OS implementations on different MTK chipsets have their own customizations and version history. All these factors lead to a large variety of encryption algorithms, albeit somewhat similar, but with nuances critical for data decryption process.
It is worth noting that some lower-level MTK devices do not implement or skip a number of modules responsible for cryptography at the hardware level. Thus, there are MTK devices with unencrypted user data, as well as MTK devices that use only software-based encryption. Prior to Android 8, this was very common.
Extraction of hardware keys
While there is no universal solution for hardware encryption support, in some cases data can still be decrypted.
Hardware keys can be extracted from the device via a special exploit that is implemented in our software. During exploitation of the vulnerability, all processes are run in RAM, meaning this action is safe since the device returns to its original state after reboot.
If the chipset is not in the list of supported chipsets, the investigator can attempt to extract the hardware keys which is typically successful. However, in this case there is a higher probability of issues arising during the password bruteforce and/or data decryption phase.
If the hardware keys have been extracted successfully but data decryption failed, the specifics of the encryption algorithm can be taken into account and its support can be added in future releases. If the MTK device under investigation is not included in our list of supported devices, try extracting data from it and then let our support team know how it went. We’ll do our best to add this case to supported ones.
Step-by-step: MTK Android data extraction
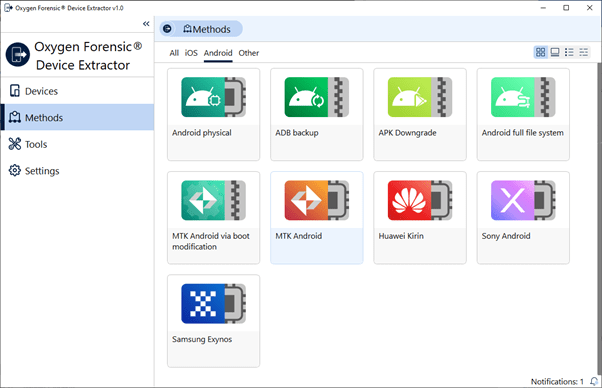
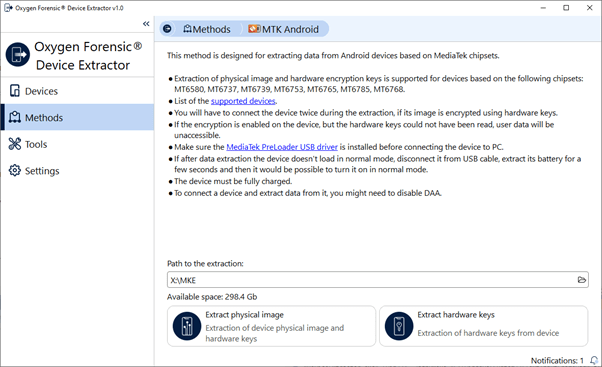
1. Select “MTK Android” in “Methods” in Oxygen Forensic® Device Extractor and follow the instructions on screen.
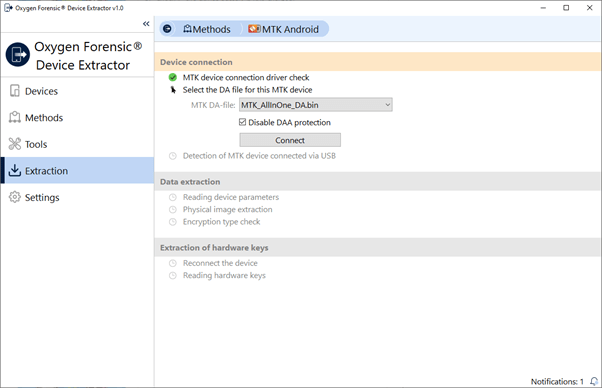
2. Set connection parameters and click “Connect”. We recommend ticking the checkbox next to “Disable DAA protection” when extracting data from devices of 2018 year and newer.
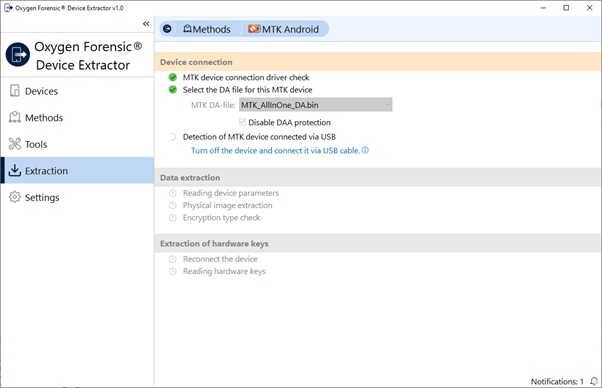
3. Connect the MTK device to the PC in accordance with the instruction.
4. Click “Start the extraction”.
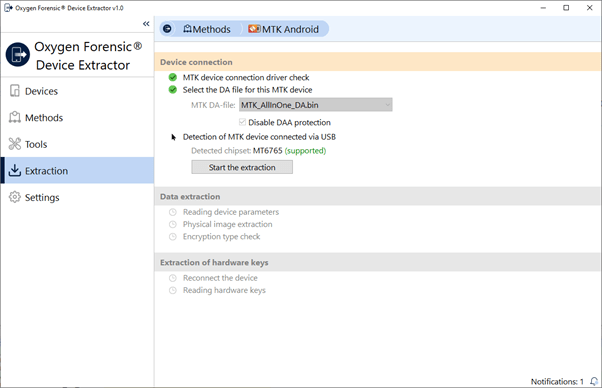
5. Wait till the reading process is complete.
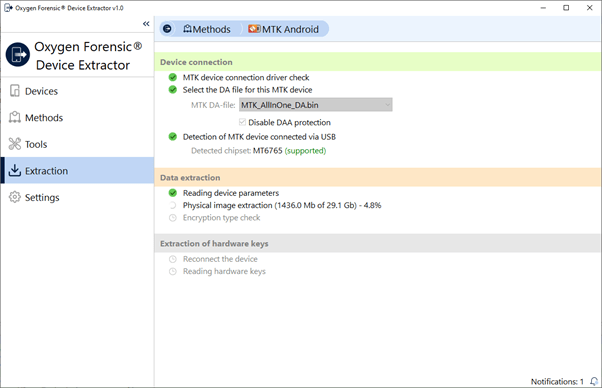
6. The exploit designed for extraction of hardware keys will be launched after the encryption type check is complete. In some cases, users might be asked to reconnect the device in accordance with the instructions.
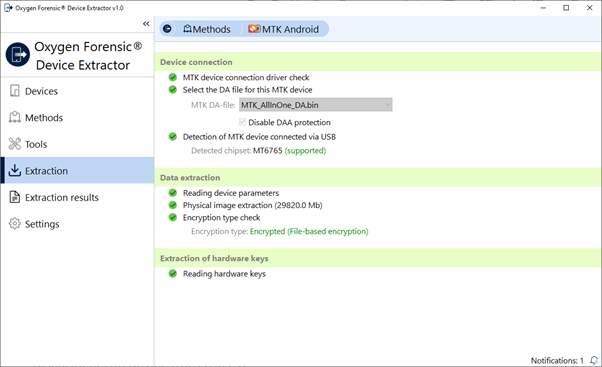
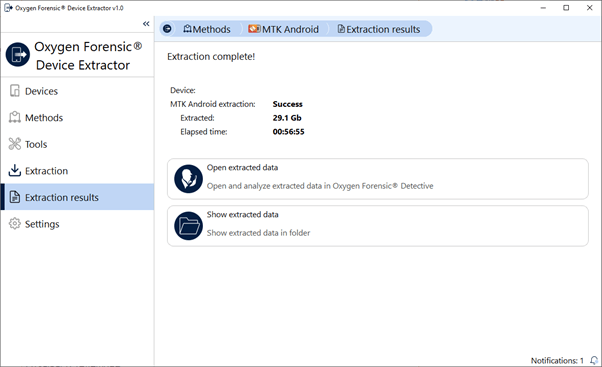
7. Click “Open extracted data”.
8. If a password is set on the device, users will be asked to enter it or start the password bruteforce process.
9. Data decryption keys will be generated.
10. Data extraction will begin.
Common Questions
How fast are password test speeds on MTK devices?
The password test speed depends on the PC’s capacity. Password bruteforce can be performed both on CPU and GPU. The test speed estimate on NVIDIA GeForce RTX 2080 Ti GPU is about 7500 passwords per second, while on Intel Core i9-9900K it is about 200 passwords per second. Thus, we recommend using modern GPUs for this task. The main parameter, on which the speed depends, is the amount of GPU memory.
What is Second Space technology?
Some Xiaomi devices implement proprietary Second Space technology. Practically, this feature creates another user space with its own set of applications and data, as well as a separate password. In this case, two passwords are required to decrypt all the data: the primary user one and the one from the Second Space. The software provides ability to bruteforce both passwords if they are unknown.
It is possible to import the image without entering the password; however, in this case most of the user data will not be available. On devices with file based encryption, BFU data can be extracted along with some media files.
What file system does MediaTek devices use?
Some MediaTek devices use F2FS instead of EXT as their file system, which has been designed to be mostly used on SSDs. Thus, the image analysis can take much longer time. For devices with large memory capacity, the difference can be several hours versus several minutes.
Get more from Oxygen Forensic® Detective
At Oxygen Forensics our solution is updated multiple times every year. We offer training courses and webinars that will help you learn the ins and outs of Oxygen Forensic® Detective and stay up to date on new features and tools needed for your investigation. Returning customer? Sign up for our newsletter to stay in the loop.
Don’t have Oxygen Forensic® Detective and want to try it out? Request a free-trial.