With more than 2.24 billion users and 100+ billion messages sent in 2020, WhatsApp is without a doubt the most popular messenger in the world.
WhatsApp popularity may stem from it being one of the most secure global messaging platforms. All messages sent using WhatsApp have end-to-end encryption and are never stored on the WhatsApp server.
It is no surprise that with this type of security it can be used to commit crimes.
It is important for investigators to have the tools to extract WhatsApp data from multiple device types and versions in all scenarios.
Table of Contents:
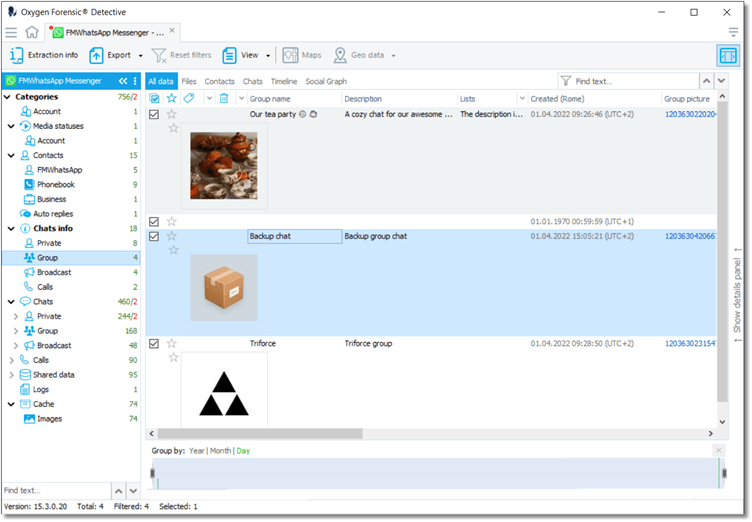
WhatsApp Extraction with Oxygen Forensic® Detective
With Oxygen Forensic® Detective investigators are able to extract WhatsApp data from mobile devices, the cloud, encrypted backups, WhatsApp Cloud server, QR Tokens from a PC, and also modified versions of WhatsApp.
WhatsApp from Mobile Devices: iOS and Android
With messaging apps like WhatsApp, investigators often face screen lock and device encryption.
End-to-end encryption implemented by WhatsApp only offers security for a “man-in-the-middle attack” or simply live interception. However, the data on an Apple iOS or Android devices is available in a decrypted format.
When it comes to iOS devices, all WhatsApp data can be extracted in a basic iTunes backup procedure. However, for Android devices, we often recommend a physical extraction method to recover WhatsApp’s evidentiary files.
With Oxygen Forensic® Detective investigators can choose from a variety of Android device physical collection methods. Keep in mind, when examining an Android device always check the SD card for a WhatsApp backup, as this file is typically encrypted.
Below is an image that shows a physical extraction of WhatsApp from an Android device.
When physical extraction is not supported for Android devices, investigators can use Android APK Downgrade or Android Agent to run a logical extraction to collect a plethora of valuable data. Android Agent is typically used to acquire basic artifacts: contacts, calls, calendars, and messages.
Also you can manually collect WhatsApp and WhatsApp Business chats, contacts, and account information using Android Agent.
Learn more about this method using OxyAgent.
WhatsApp Modified Versions
A WhatsApp mod apk is a modified version of the WhatsApp application. They are designed by third-party developers or individuals who want to incorporate additional functionality to the official WhatsApp version. There are a total of 10 modified versions, Oxygen Forensic® Detective supports extraction of 3 of these modified versions from Android OS devices.
Oxygen Forensic® Detective can extract data from:
- GB WhatsApp
- FM WhatsApp
- OB WhatsApp
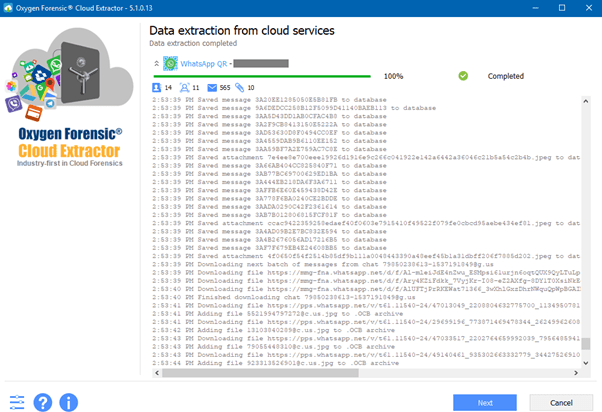
WhatsApp From Cloud
A WhatsApp user, using an iPhone or Android device, may choose to back up their chats to iCloud or Google Drive.
It is important to understand that WhatsApp backups are encrypted by default and to decrypt them a forensic investigator needs access to the SIM card. With the SIM an investigator can recover and decrypt WhatsApp data associated with that card.
When extracting WhatsApp data from various cloud services, there could be additional hurdles like two-factor authentication (2FA) or two-step verification. The Oxygen Forensic® Cloud Extractor can help overcome these challenges.
Extraction of this cloud data can be extremely important to an ongoing case. This collection may contain data that had been deleted from the device which can occur if synchronization is set to each week or each month.

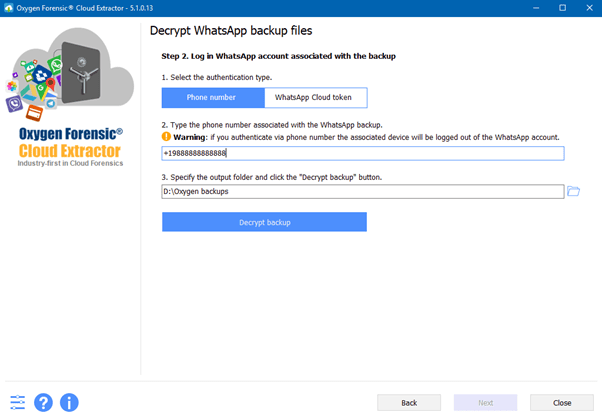
WhatsApp Backup Decryption
The standard WhatsApp backup decryption method used throughout the industry is based on a key file. With our innovative methods, Oxygen Forensics offers a new decryption process that requires only a phone number. This method is a great alternative to the commonly used key file.
For example, if you have found an encrypted backup on an Android’s SD card with no access to the Android internal memory. What do you do?
Oxygen Forensic® Cloud Extractor offers you an exclusive opportunity to decrypt this backup by receiving a code to the phone number assigned to the recovered SIM card.
Not only is the data from the device recoverable, but Oxygen Forensic® Detective can also recover a special WhatsApp Cloud token from physical extractions of Android devices.
This token can be utilized to decrypt WhatsApp backups from Android devices, WhatsApp Google Drive, and WhatsApp iCloud backups associated with the same phone number.
WhatsApp Cloud (Server)
It is known that WhatsApp does not store any communications on its server that have been delivered. Messages and unanswered calls that cannot be delivered (e.g., it has no Internet connection, or it is switched off) will be temporally stored on the server.
Oxygen Forensic® Detective has the unique ability to access this data from the cloud via only the phone number or special WhatsApp Cloud token extracted from Android devices.
Recommendation:
If you have a locked mobile device that you cannot acquire, try this: switch it off, wait for a few moments, remove the SIM card, and place it into another phone that is unlocked to a carrier.
Select WhatsApp Cloud service in our Cloud Extractor, then select to receive a code to the SIM card.
Now you will have access to the undelivered messages, unanswered calls, and their contacts.

WhatsApp via QR Token from PC
WhatApp users can communicate using WhatsApp Desktop and WhatsApp Web Apps from a computer. Research of where WhatsApp stores this data has revealed that WhatsApp does not store any data on the computer that is being used.
However, the Oxygen Forensic® KeyScout utility, built into Oxygen Forensic® Detective, can detect a WhatsApp QR token on a computer where WhatsApp was used. The QR token will allow investigators to extract complete WhatsApp data in our Cloud Extractor. The only condition is that the WhatsApp owner’s mobile device must have an active Internet connection.
If the mobile device is locked the WhatsApp QR code method will still work.
If you have an unlocked mobile device but the extraction continually fails, scan the WhatsApp QR code from the device you want the WhatsApp data from in our Cloud Extractor to acquire all the data.