In Oxygen Forensic® Detective v.15.2 we have enhanced support for Linux devices by making data collection easier for our users and added support for the XFS file system that is frequently used in the newest Linux versions.
KeyScout can now extract from Linux-operated devices:
Let’s take a look at how these features work in Oxygen Forensic® Detective.
Extraction of Cron tasks
Cron is a classic program in Unix systems that runs in the background and is used to periodically perform tasks at specified times. Regular actions are described by instructions placed in “Cron” tab files. These files are created for the system itself and for each user.
Investigators with Oxygen Forensic® Detective can now learn more about Cron tasks.
Cron data will be extracted automatically unless the artifact is excluded from the search. To add it, open “Search settings” then go to the “System artifacts” tab and tick the checkbox next to “Cron”.
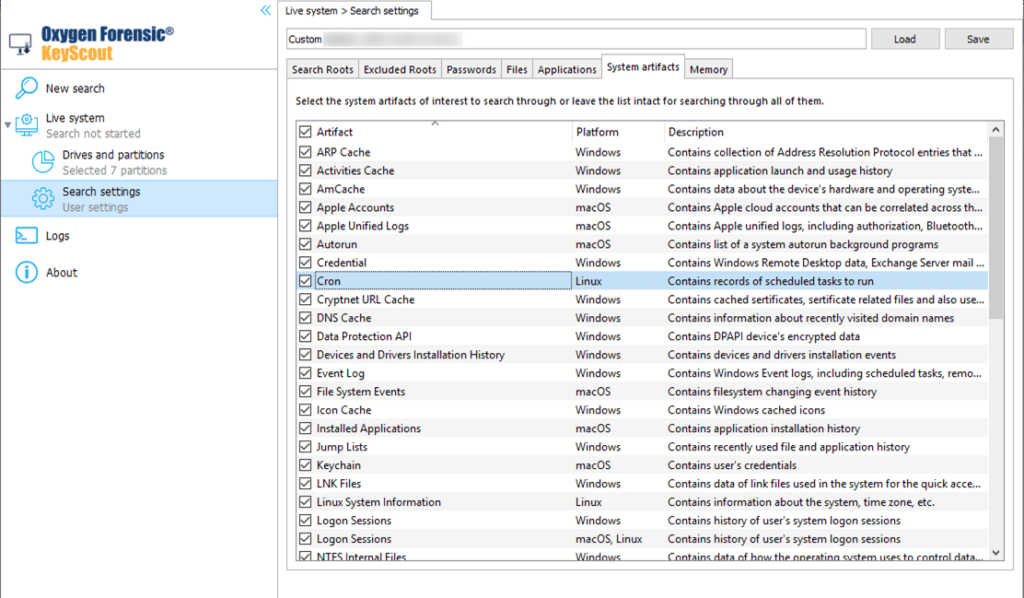
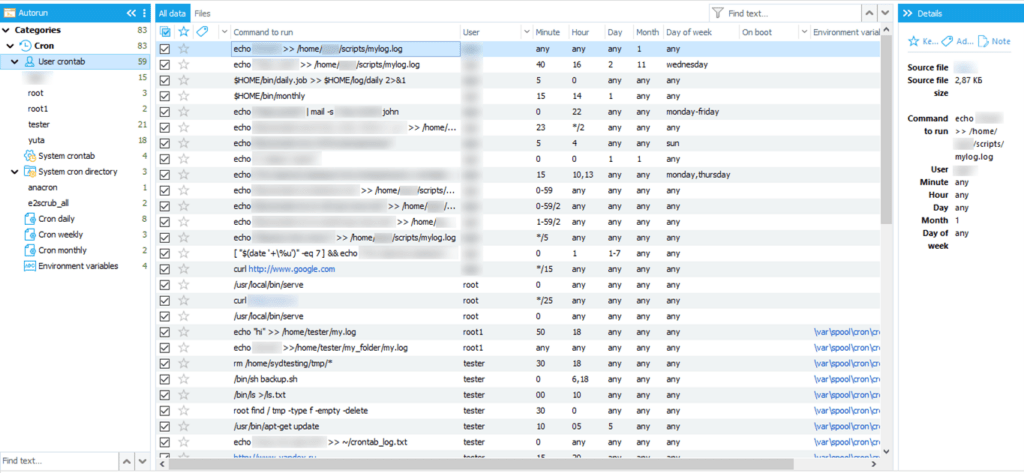
As soon as data extraction is complete, open the “Cron” category within the “Autorun” section to view the results, which may include the following:
- User Cron tab files
- System-wide schedule stored in Crontab file
- System-wide schedule stored in files
- Daily executed Cron files
- Monthly executed Cron files
- Weekly executed Cron files
- Information about managing task output
Extraction of SSH keys
The primary method of remote management on Linux and macOS systems is the Secure Shell (SSH) protocol. This mechanism supports several authentication methods, including authorization by credentials or via cryptographic keys.
Authentication via cryptographic keys has several advantages:
- it is more secure and is often the only enabled authorization method
- it is stealthy, allowing adding the key unnoticed in case of an emergency
- it is not related to the user’s password
In Oxygen Forensic® Detective v.15.2, we have added support for extraction of SSH keys from Linux and macOS. The keys will be extracted automatically, unless the artifact is excluded from the search.
To add it, open “Search settings” then go to the “System artifacts” tab and tick the checkbox next to “SSH keys”.
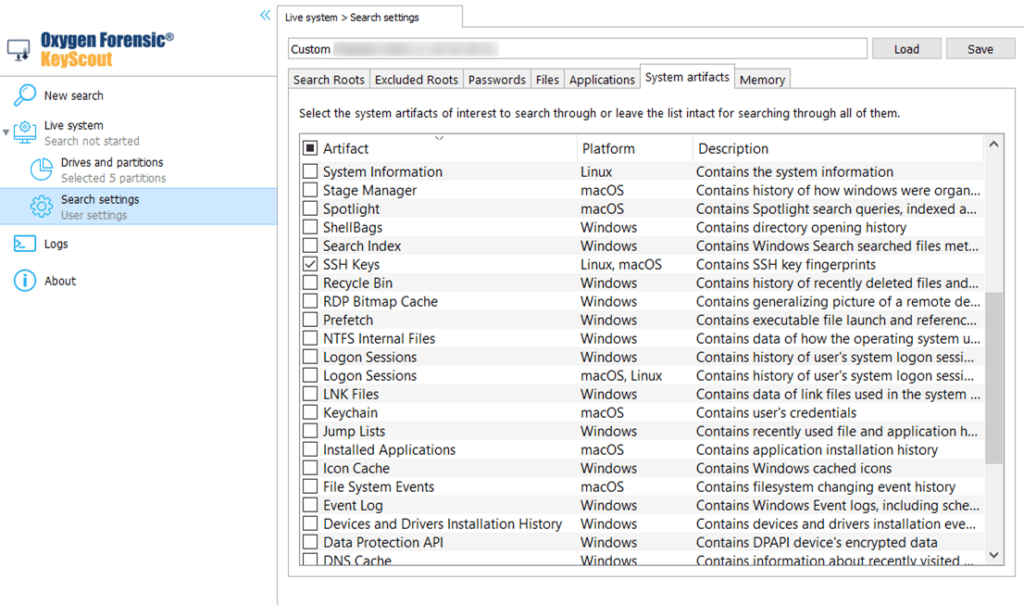
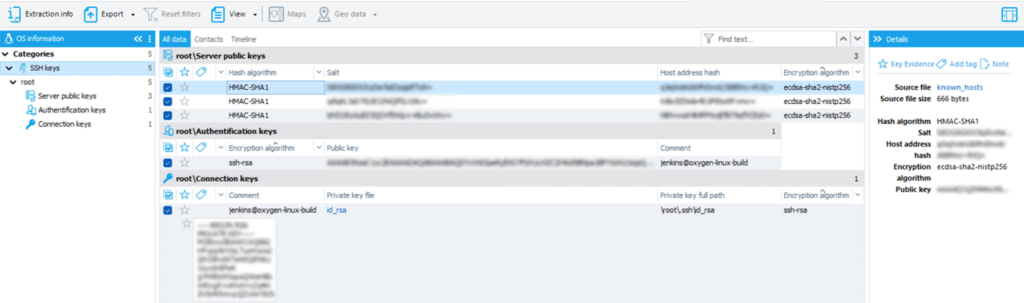
As soon as data extraction is complete, the following data may be displayed in the “SSH keys” category within the “Information about the OS” section:
- Server public keys. This category contains information about all known remotely connected hosts.
- Authentication keys. This category contains information about key fingerprints that allow logging into the user’s account.
- Connection keys. This category contains information about public and private keys.
Extraction of information about system accounts and groups
Linux user accounts have a certain set of properties that define their capabilities. These properties include:
- user type (root, system, and regular)
- numeric ID
- password
- group membership
- home directory
In Oxygen Forensic® Detective v.15.2, we have added support for the extraction of user accounts from Linux.
The data will be extracted automatically unless the artifact is excluded from the search. To add it, open “Search settings” then go to the “System artifacts” tab and tick the checkbox next to “User accounts”.
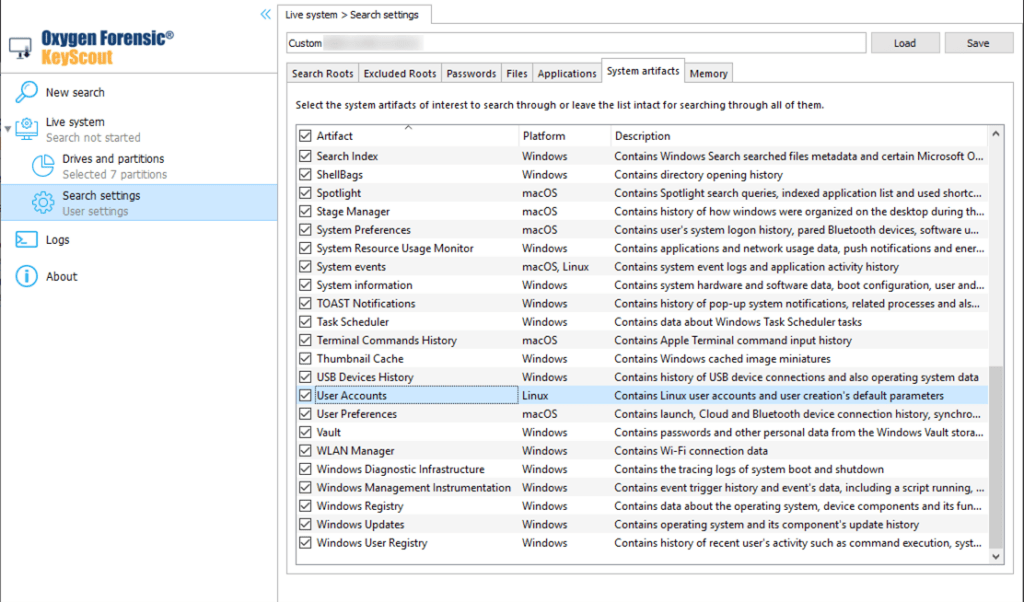
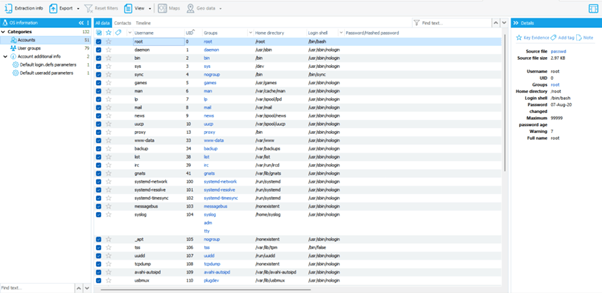
As soon as data extraction is complete, the following data may be displayed in the “Information about the OS” section:
- This category contains information about accounts and passwords of the system, local, and root users.
- User groups. This category contains information about user groups and their passwords.
- Default login.defs parameters. This category contains login.defs parameters used by default when creating new users.
- Default useradd parameters. This category contains information about options from the useradd file that are used by default when creating new users.
- Default etc/skel files. This category contains files that are added by default to the home directory of the newly created user, if the default folder has not been changed by the user.
Get more from Oxygen Forensic® Detective
At Oxygen Forensics our software is updated multiple times every year. We offer training courses and webinars that can help you learn the ins and outs of Oxygen Forensic® Detective and stay up to date on new features and tools needed for your investigation. Returning customer? Sign up for our newsletter to stay in the loop.
Don’t have Oxygen Forensic® Detective and want to try it out? Request a free-trial.