Oxygen Forensic® KeyScout is a built-in module of Oxygen Forensic® Detective that extracts data from macOS, including pre-installed Apple apps, user-installed apps, system files, and user credentials.
Let’s take a look at macOS system artifacts that are supported by Oxygen Forensic® KeyScout.
System Artifacts Extracted with Oxygen Forensic® KeyScout
Oxygen Forensic® KeyScout can extract the following system artifacts from macOS:
- macOS Filesystem Events
- macOS User Preferences
- macOS System Preferences
- macOS Autorun
- macOS Spotlight
- System events
- Apple unified logs
- Terminal Commands History
- Apple accounts
- Logon Sessions
- Installed Applications
- Keychain
Investigators can extract all the system artifacts or select several ones in the KeyScout Search Settings.
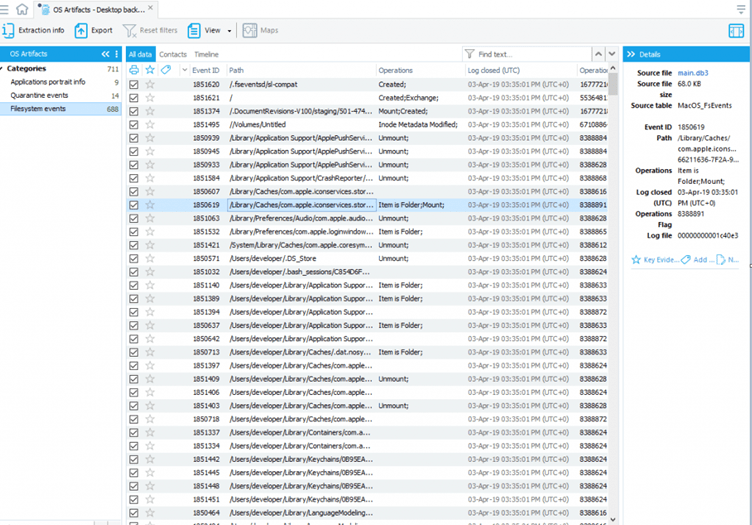
macOS Filesystem Events
FSEvents files store all the activity regarding the computer filesystem and include records related to deleted or unmounted files and disks. Please note that FSEvents can be found in the system folder and require root privileges, meaning the root user must be enabled on the Mac where the investigator is going to collect FSEvents files.
FSEvents analysis is useful for:
- Establishing which files the user opened, modified, or deleted at a certain time period
- Establishing the usage of removable media and data transfer from/to removable media
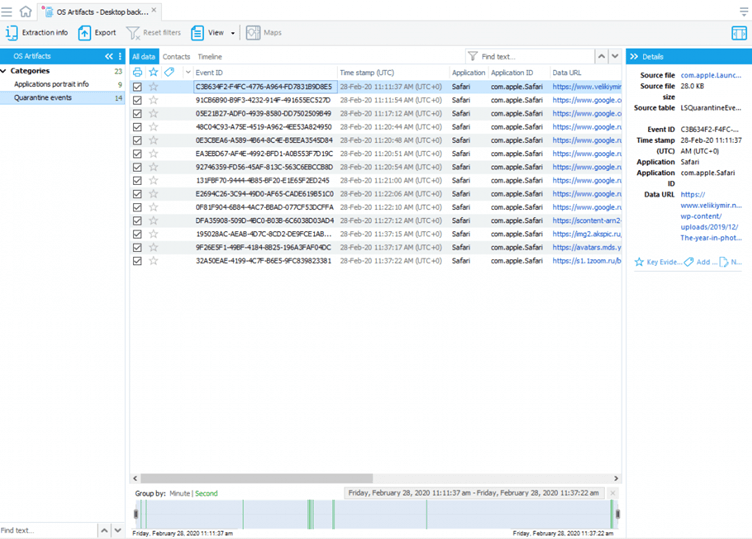
macOS User Preferences
QuarantineEvents keeps a log of all the user’s downloads coming from all possible external sources, including files received from the Internet or via AirDrop. QuarantineEventsV2 files are separate for each user on the system. It’s important to note that Quarantine data is preserved even if related files were deleted from the system. QuarantineEvents analysis is useful for:
- Tracing file origins
- Tracing malware infections
- Determining which files were shared by users
Additionally, under the User Preferences, the Finder data is parsed. The Finder is the first thing that a user sees when a mac starts up. The parsed Finder data will include recent move and copy destinations, tags, go to folders, and recent folders.
Overall, this artifact provides useful insights into the recently used files and folders.
macOS System Preferences
The parsed macOS system preferences may include the following information but not limited to:
- System updates
- Wi-Fi connections
- Paired Bluetooth devices
- Connected iOS devices
- Keyboard settings
- Network settings and VPN connections
- Synchronized contacts
macOS Autorun
These system artifacts include the information about autorun apps that are launched at the system startup.
macOS Spotlight
Spotlight is used to find items on mac, like files, apps, or emails. Once this artifact is parsed in our software, investigators will see the list of recently accessed shortcuts with the original query and last used in Spotlight time stamp.
System events
If investigators need to analyze daily, weekly, monthly, or system logs, they can select extraction of the system events artifact. It includes plain-text files from /var/log and /private/var/log.
Apple unified logs
Apple unified logs contain hundreds of various events that may include information about external connected devices, user authorizations, system notifications, Bluetooth connections, and other valuable pieces of evidence.
Terminal Commands History
Once this artifact is parsed, investigators will be able to analyze the history of commands that were run in the terminal.
Apple accounts
This artifact will contain information about all the user accounts found in the system: iCloud, Mail accounts, and others.
Logon Sessions
The logon sessions include information about users and their login date and time.
Installed Applications
The information about installed applications is of vital importance for malware analysis. Every app in the list will have its identifier, installation path, and version.
Keychain
Keychain securely stores passwords and account information on mac devices. Our software parses keychain data only while live extraction is done. Please note that keychain parsing from the latest macOS is not supported yet.
Conclusion
Being able to extract system artifacts is important because it can show investigators a lot of information like specification documents, design documents, source code, and any information needed about the operating system.
Want to try Oxygen Forensic® KeyScout to extract system artifacts? Contact us for a free trial license.