What is BitLocker?
BitLocker is a full-volume encryption feature included with Microsoft Windows versions starting with Windows Vista. It is designed to protect data by providing encryption for entire volumes. By default, it uses the AES encryption algorithm in cipher block chaining (CBC) or XTS mode with a 128-bit or 256-bit key. CBC is not used over the whole disk; it is applied to each individual sector instead. A disk or its partition can be encrypted with the help of this technology.
BitLocker Encryption Details
Data encryption is performed according to a complex scheme, which involves several encryption levels with different encryption keys:
Full Volume Encryption Key (FVEK) and AES-128-CBC, AES-128-XTS, AES-256-CBC, and AES-256-XTS are used for the encryption of user data stored in a BitLocker-protected partition. The FVEKFull Volume Encryption Key is generated once upon creating a protected disk partition and does not change. It remains the same even if the password to the disk gets changed.
The FVEK is stored on the disk in encrypted form, protected with the Volume Master Key (VMK). The VMK changes each time when the partition protection type gets changed.
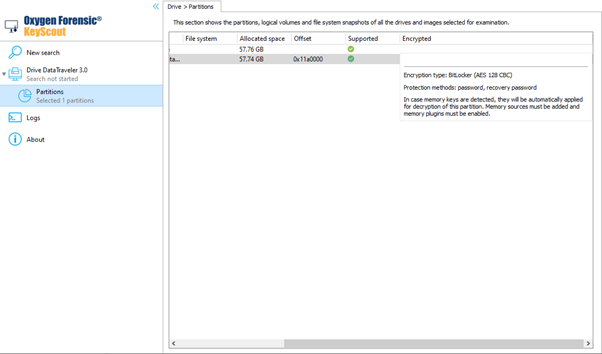
The VMK is stored on the disk in encrypted form in multiple copies. Each copy is encrypted with the use of a protector. Protectors are used to decrypt the disk with the help of a password, smart card, or backup recovery key. Each protector offers a different way to decrypt the VMK and the disk content. For the decryption to be successful, a password, smart card, or recovery password, also known as secrets, will be needed from each protector.
The main protector types are:
- Password is the most popular protector type. This can be bruteforced if needed.
- Recovery password is yet another opportunity to disable the protection. The OS generates the key automatically once the encryption is enabled and offers the option to save it to a file, cloud, Active Directory, or print it. Files protected with this key type can easily be detected automatically.
- TPM is a protection type with the use of a hardware encryption module. With no password set, the disk is automatically decrypted if it is connected to the computer on which it was encrypted. It is impossible to decrypt this protector type on another computer.
- TPM + PIN is a protection type with the use of a hardware encryption module strengthened by a password. Successful decryption of this protector requires decryption on the same computer that the drive was encrypted on, as well as knowledge of the PIN. Due to the use of TPM, this PIN cannot be bruteforced.
- External key. Some protectors utilize external keys, such as USB-devices, smart cards, and domain controllers. Access to the external key is required for decryption of such protectors and bruteforce is impossible.
BitLocker support in Oxygen Forensic® Detective
Starting with version 15.5 of Oxygen Forensic® Detective v.15.5, investigators can use Oxygen Forensic® KeyScout to extract BitLocker keys and analyze disk partitions protected with BitLocker.
BitLocker partitions are encrypted via Full Volume Encryption and Volume Master Keys with the use of a password or a recovery password. Other protectors are not yet supported. Both keys can be extracted from RAM, RAM images, or hibernation files.
When Windows OS utilizes BitLocker-protected partitions, the Full Volume Encryption and the Volume Master Keys (which are used for reading and opening files from the protected partition) are stored in RAM. If a RAM image is made when some partitions are unlocked or analyze live system at that time, Oxygen Forensic® KeyScout can detect both keys by their signatures in RAM and save them to the backup for future use.
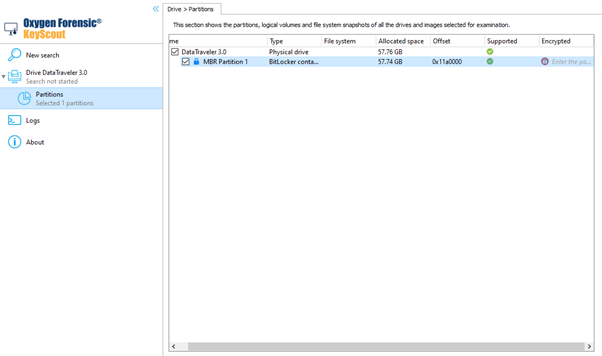
Please note that Oxygen Forensic® KeyScout only extracts keys, not information about the partition it has been used to encrypt. With this in mind, if there are several BitLocker encrypted partitions in the system, the keys found will need to be applied to all those partitions to determine which partition a particular key fits.
The extraction process and results are influenced by the state the protection is in.
- If the partition is protected and encrypted, the knowledge of keys from an external source or one of the protector’s secrets is required.
- If the partition is protected and unlocked within the current session of the “live” system, the partition has already been unlocked and the key is stored in RAM. In this case, Oxygen Forensic® KeyScout can use the operating system API to access the unlocked partition data even without knowing the keys or protectors. Oxygen Forensic® KeyScout can also retrieve the keys from RAM.
- If the partition is encrypted, but not protected, this means that the protectors are disabled or deleted. In this case, although the data is encrypted with the use of the Full Volume Encryption key, the key can be extracted from the disk without requiring the knowledge of any protectors. If this is the case, Oxygen Forensic® KeyScout displays that the partition is protected by BitLocker but has been decrypted successfully. The decryption is performed automatically and no additional actions are required from the user.
Get more from Oxygen Forensic® Detective
At Oxygen Forensics, we continuously update our software to ensure we stay at the forefront of digital forensic technology. We offer training courses and free webinars that can help you learn the ins and outs of Oxygen Forensic® Detective and stay up to date on the latest features and tools needed for your investigation. Returning customer? Sign up for our newsletter to stay in the loop.
