
In investigations, time is extremely significant. We are constantly looking for new methods of data extraction that will permit forensics experts to receive results in the shortest time possible. In October of 2018 we released our support for QR code token extraction to assist in the speed and efficiency of cloud data extraction from WhatsApp. We realized that when time is a factor, it is easiest to scan a QR code with the subject’s phone using Oxygen Forensic® Cloud Extractor and quickly obtain the required evidence.
We introduced WhatsApp QR code authorization first and this method is located under WhatsApp QR service in the Cloud Extractor. Continual innovation has allowed us to bring even more support to our customers for this method. We have since added QR code support for the following services:
- Viber (under Viber Cloud)
- Line
- Line Keep
- Telegram
- Telegram Passport
- Huawei Cloud
We expect our list of supported cloud services to grow as more apps start using QR code authorization.
Extraction methodology is the same for all our supported services. Investigators need to have the subject’s device unlocked and connected to the Internet.
Given that WhatsApp is one of the most popular messaging apps, let’s use it as an example and go through the data extraction process step by step:
1. Open Oxygen Forensic® Detective and click on Oxygen Forensic® Cloud Extractor on the Home screen to run the built-in Cloud Extractor.
2. Start a new extraction and find WhatsApp QR in the list of all supported cloud services.

3. Next, press the Add Credentials button and select the QR code option. Open WhatsApp on the subject’s device and go to the WhatsApp Web/Desktop option in Settings. Press the Validate button in the Cloud Extractor and scan the QR code with the device.
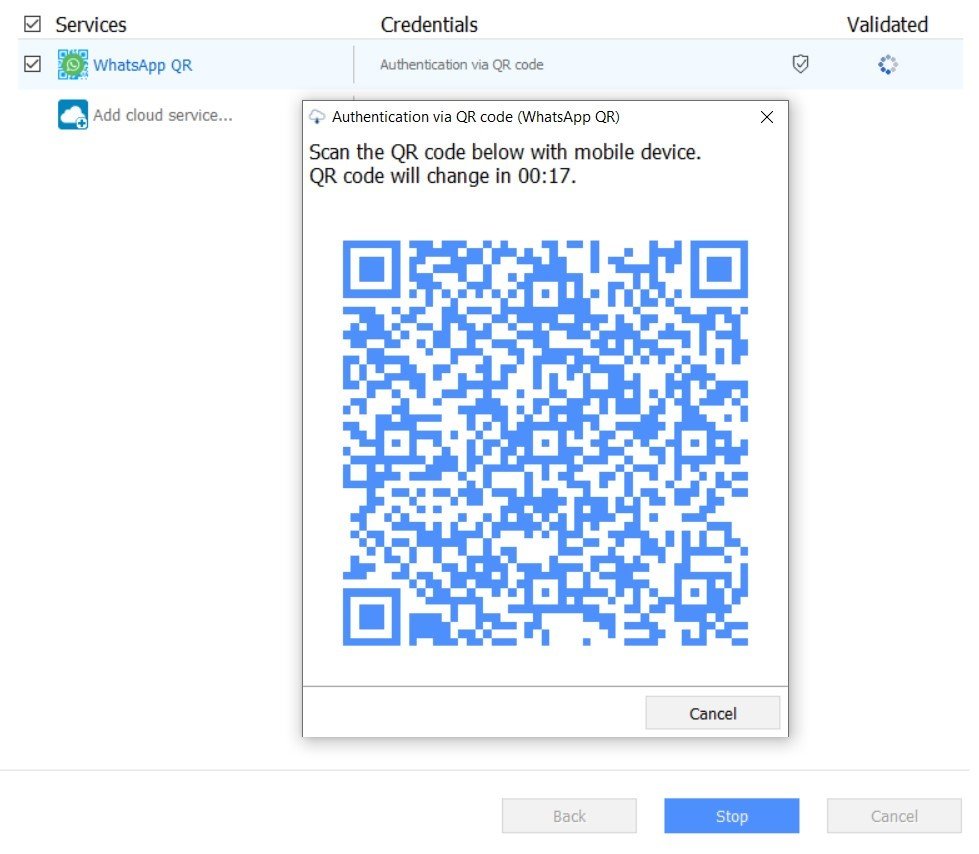
Once authorization is granted, there will be an entry in the WhatsApp Web/Desktop menu indicating the time, place, and device OS that is now using WhatsApp via QR code. Once the data extraction is complete, terminate the session in WhatsApp and the entry will be erased from the WhatsApp Web/Desktop menu.
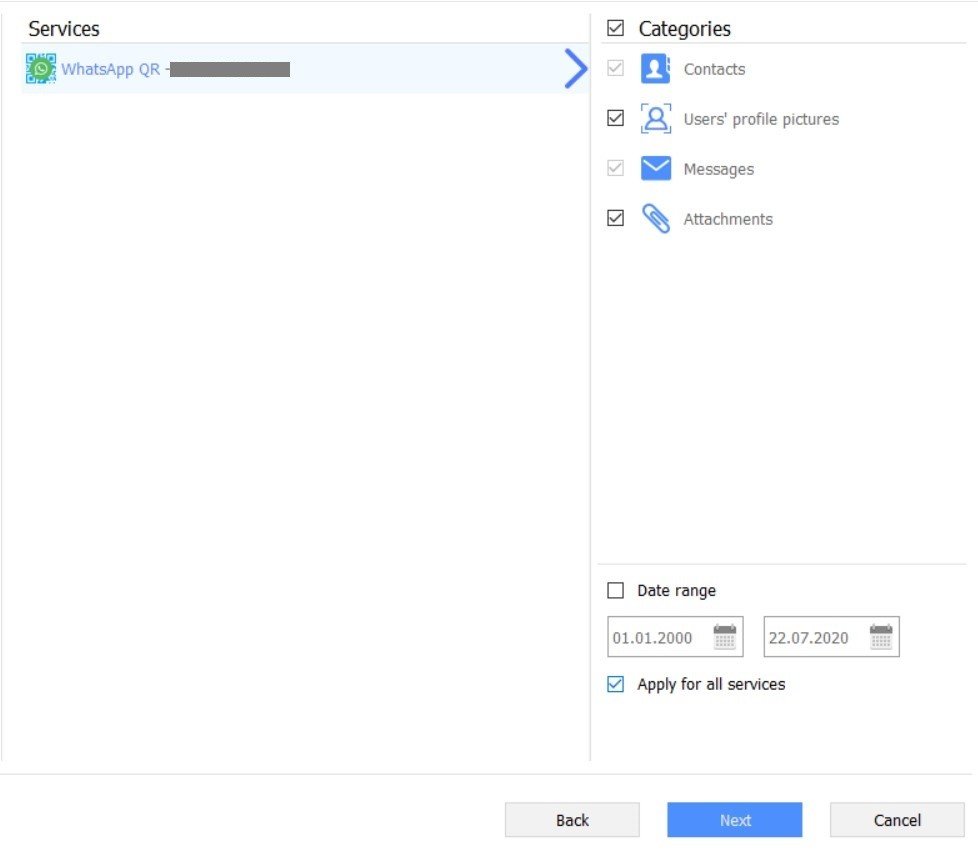
4. In Oxygen Forensic® Cloud Extractor, select artifacts that you wish to acquire and set the date range for the extraction. Press the Next button to begin the extraction.
5. Once data is extracted the investigator will see the final screen, which will present the option to import the extraction into Oxygen Forensic® Detective or save it to OCB backup to be imported later into Oxygen Forensic® Detective using another computer. No matter what option is chosen the user will have extracted WhatsApp data into the Oxygen Forensic® Detective interface, as shown below.
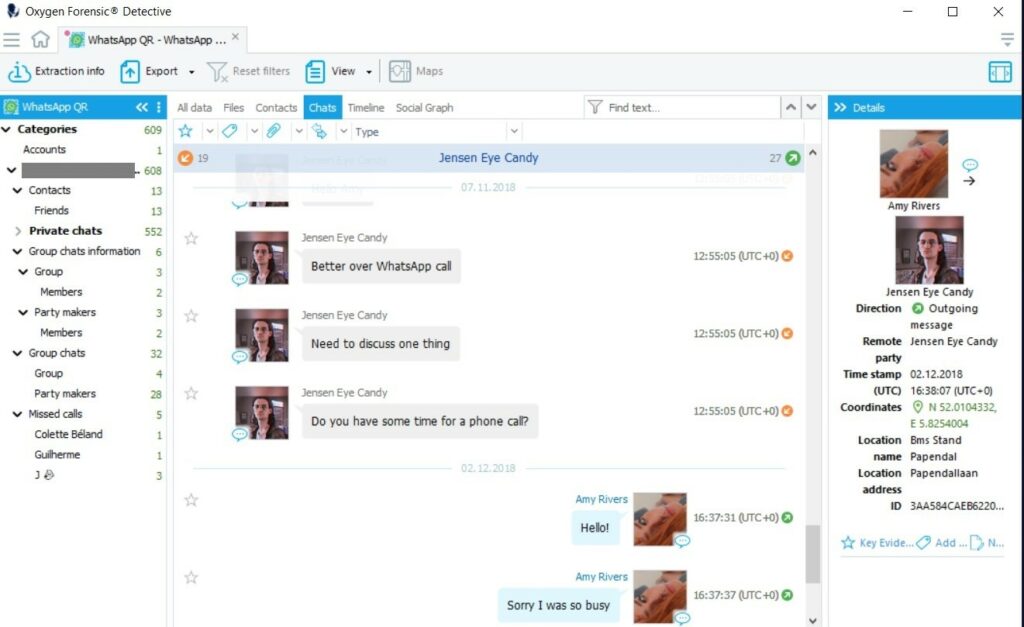
Like with all other extraction, users can merge this WhatsApp QR extraction with others for further analysis or simply open them in the built-in analytical section, which includes analysis via Social Links, Timeline, Statistics, and more.
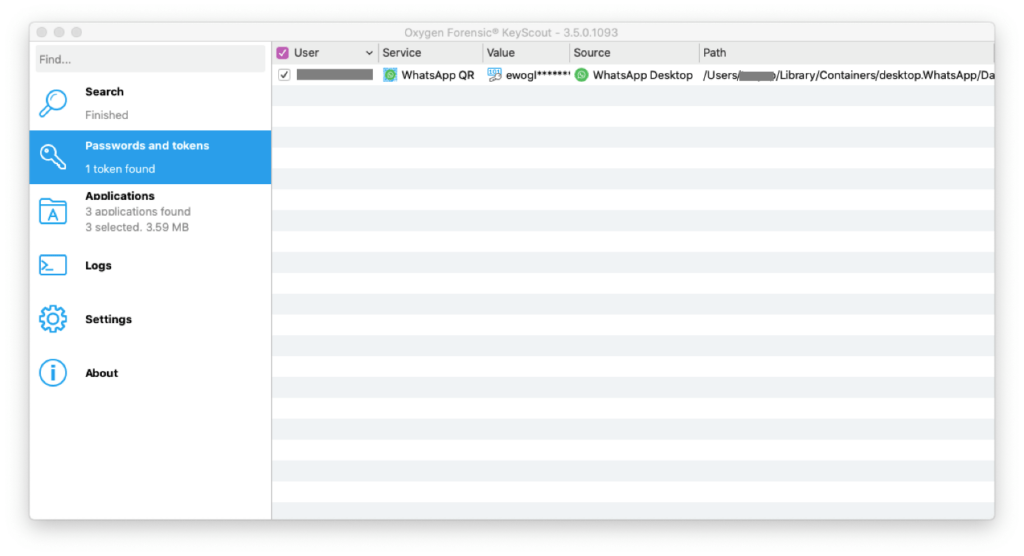
Our use of the QR technology does not stop here. If an investigator has access to a Windows or macOS computer, in which WhatsApp Desktop or WhatsApp Web apps were used, they can run our portable Oxygen Forensic® KeyScout utility to collect a WhatsApp QR token. Using this token, investigators can complete a full WhatsApp extraction using our Oxygen Forensic® Cloud Extractor. This method is extremely beneficial since no WhatsApp data is generally stored on target computer. An investigator can often find some artifacts in the web browser extraction, if WhatsApp Web was used, but there is no way to extract the complete WhatsApp data from computers. As a result, our extraction method based on WhatsApp QR token will surely benefit future investigations.
Interested in trying out this advanced functionality? Ask us for a demo license here.