Oxygen Forensic KeyScout is a portable utility available at no additional charge within Oxygen Forensic Detective software. It allows searching and extracting data from a running computer system using OS API calls and user privileges. You can find the KeyScout utility on the Oxygen Forensic Detective home screen. Once located investigators simply copy the executable to a removable drive and then run it on the subject’s Windows, macOS or Linux computer. Oxygen Forensic KeyScout collects a wide range of data, including user credentials, data from Email clients, Messengers and Web Browsers.
KeyScout included in Oxygen Forensic Detective 12.3 brings significant enhancements that can be used for both criminal and corporate investigations that include employee misconduct investigation, malware infection analysis, incident response, etc. The updated KeyScout allows investigators to recover insights into computer usage by collecting important system files on Windows and macOS computers. Let’s have a look at all these files and how this information can assist in an investigation.
System files on Windows PC
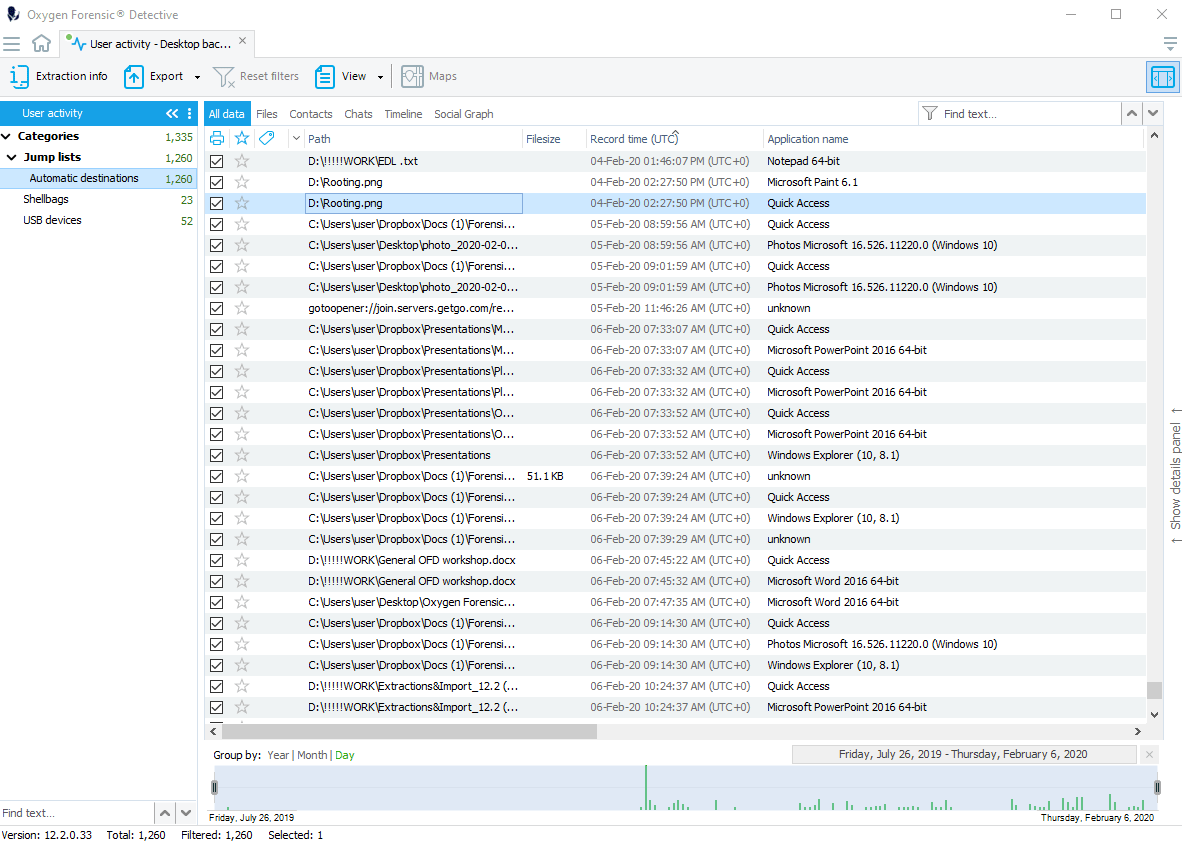
1.Jump Lists
Jump Lists contain the history of the user’s recent interactions with the computer, for example, file or folder selection, file opening, etc. For each application there is a separate file located in the following hidden directory: Users<username>AppDataRoamingMicrosoftWindowsRecent items
The forensic value of these files is enhanced by the fact that Jump Lists are preserved even if related files are deleted.
Once KeyScout finishes scanning investigators simply save the extraction to removable media and open it later on the computer where Oxygen Forensic Detective is installed. Investigators should choose “Oxygen Desktop backup” for KeyScout extraction import. All the Windows system files mentioned in this article can be located in the User activity section in Oxygen Forensic Detective.
The extracted data contains: Application ID and name, Record time, Full path to the chosen file or directory, File size, Created/Last modified/Last access time stamps.
Jump Lists analysis provide:
- outline of what the user was doing at specified time interval
- insights into the usage of certain applications
- proof that certain files and directories were accessed by the user
- opportunity to trace the origin of certain files
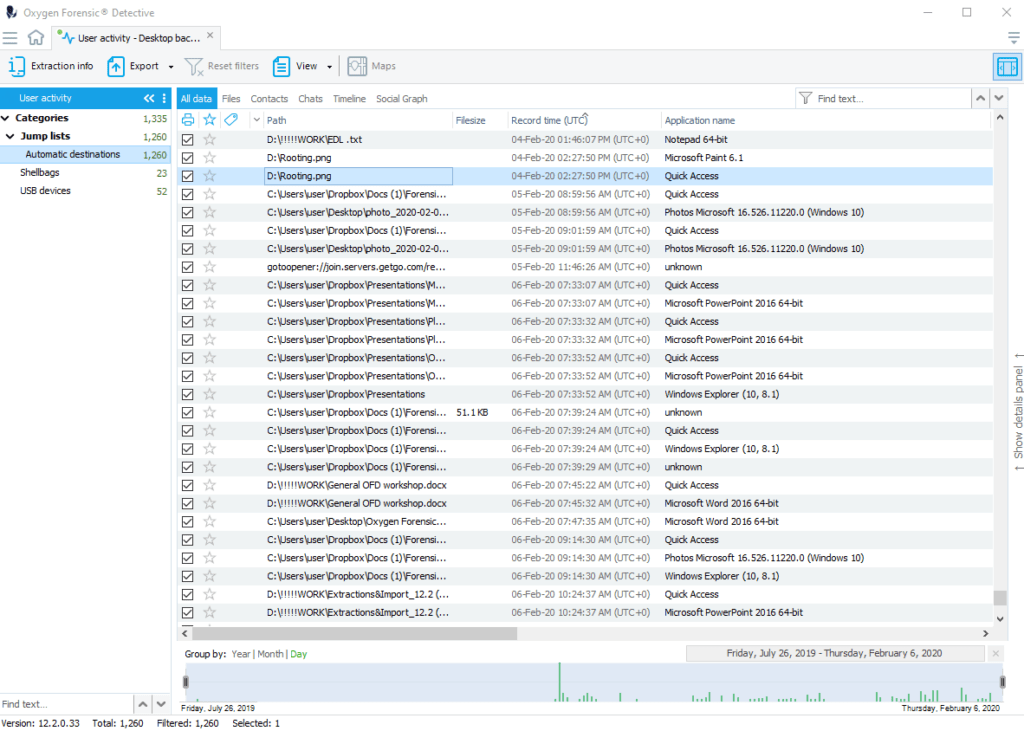
2.Shellbags
Shellbags allow the investigator to track the folder browsing history of the user and get the details of a folder that might no longer exist. Whenever user opens any directory in Windows Explorer, parameters of this directory are saved in Windows Registry in ShellBag data format. Since ShellBags are kept indefinitely even if related directories are deleted or inaccessible this artifact can be a gold mine!
The extracted data contains: full path to accessed object, date of last visit, and attributes of accessed object.
Shellbags analysis provide:
- outline of what the user was doing at specified time interval
- proof that certain files and directories were accessed by the user
- opportunity to trace the origin of certain files
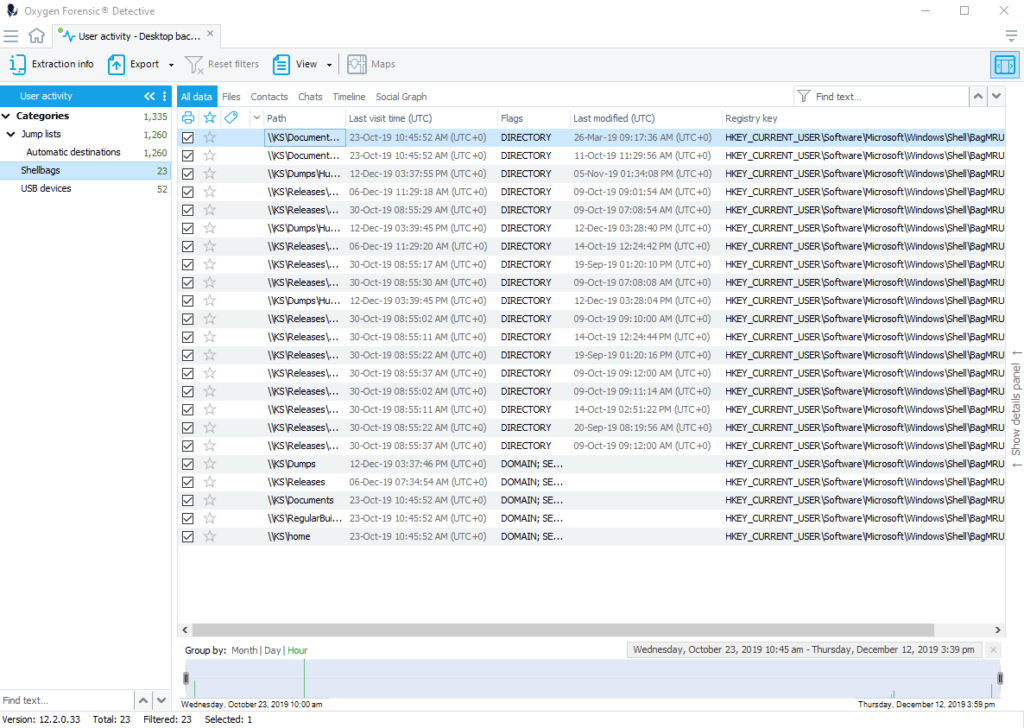
3.USBSTOR
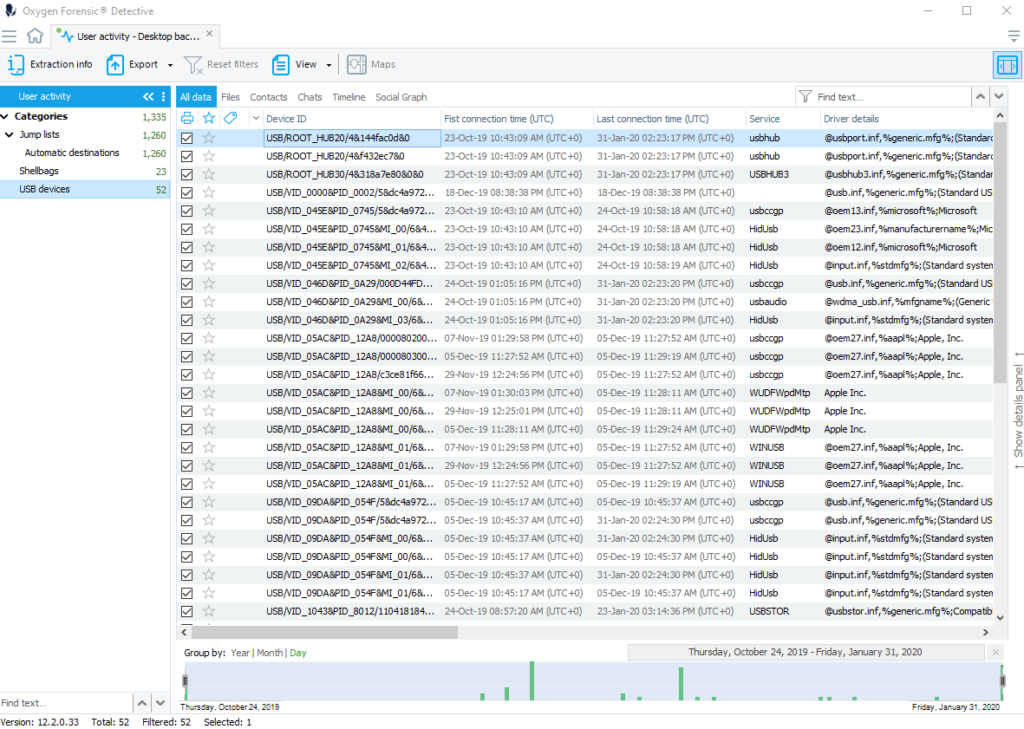
Whenever a USB device is connected to the Windows computer, the information about the device is saved in the Windows Registry and kept there indefinitely. The USBSTOR file contains the history of all USB connected devices.
The extracted data contains: Device model, Device serial number, Device description, First and last time device connection, and extended device information.
USBSTOR analysis allows investigators to:
- Find origin of malware infection
- Establish channel of data leak
- Get information on external devices used by the suspect
System files on macOS
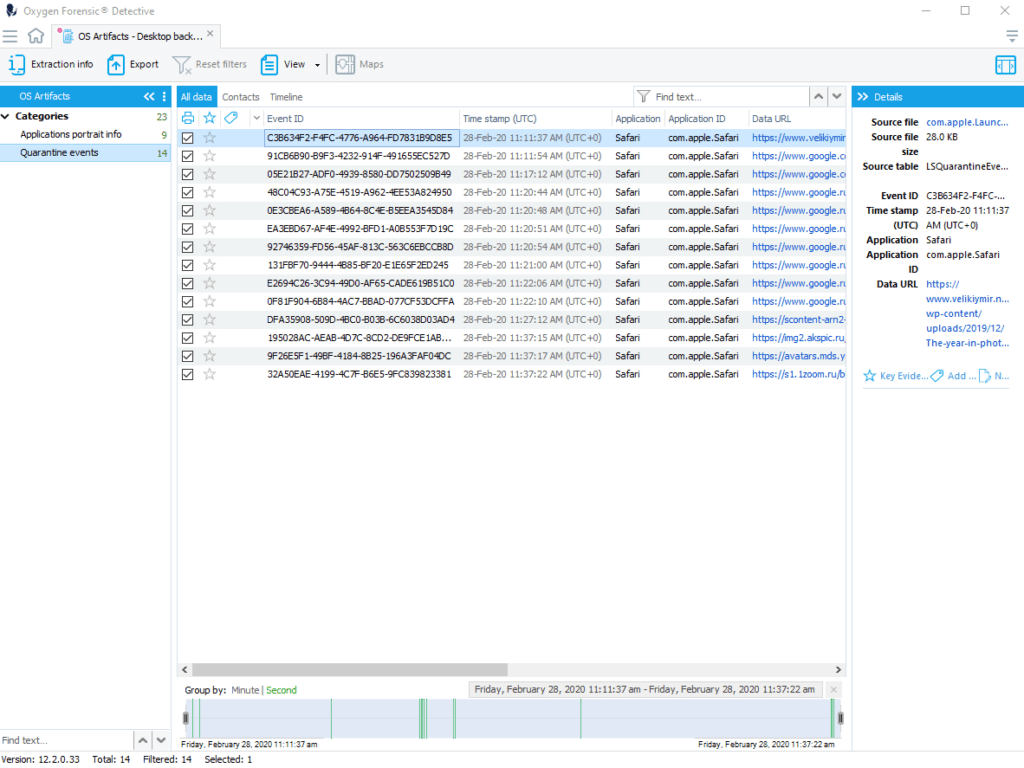
1. Quarantine Events
QuarantineEvents keeps a log of all the user’s downloads coming from all possible external sources, including files received from Internet and via AirDrop. QuarantineEventsV2 files are separate for each user on the system. What is important is the fact that Quarantine data is preserved even if related files were deleted from the system.
The extracted data includes the File ID, Quarantine timestamp, Source application name, Source type and other information.
All the macOS system files mentioned can be found in the OS artifacts section in Oxygen Forensic Detective once a KeyScout extraction is imported into the software.
Quarantine Events analysis is useful for:
- tracing origin of files, including cases of malware infection
- determining which files were shared by users
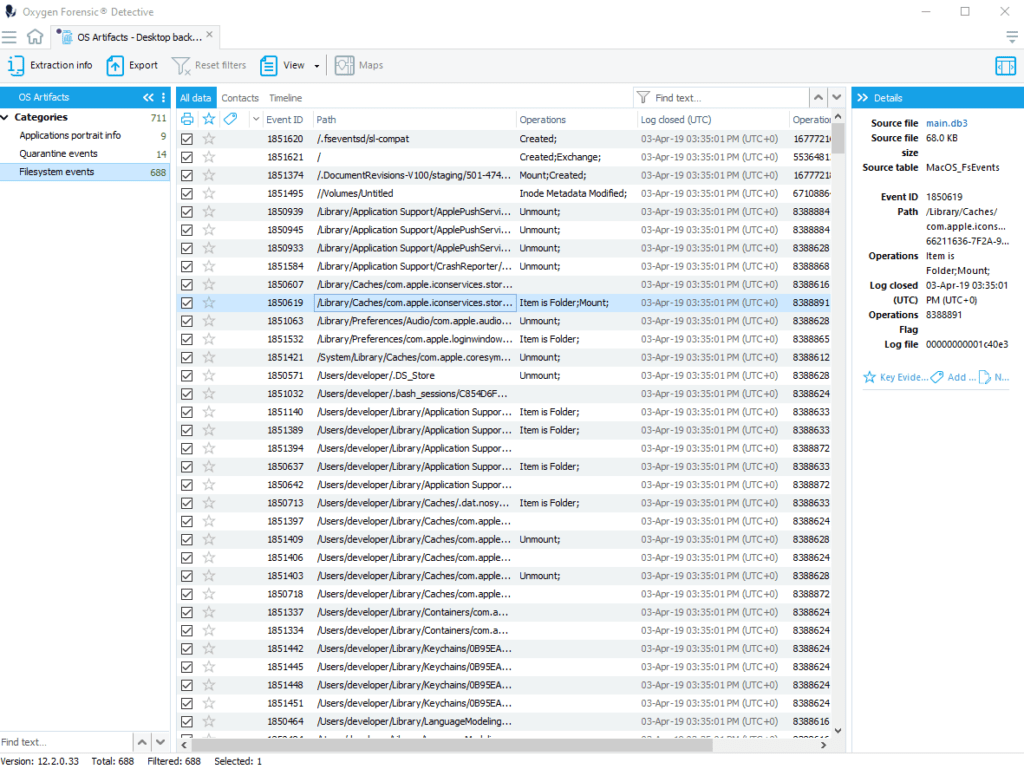
2.FSEvents
These files store all the activity regarding computer filesystem and include records related to deleted or unmounted files and disks. Please note that FSEvents can be found in the system folder and require root privileges. This means that the root user must be enabled on the mac where the investigator is going to collect FSEvents files.
The extracted data contains: Event ID, Path to object, Type of object: file, directory or volume, List of operations, Filesystem node ID and Time interval.
FSEvents analysis is useful for:
- Establishing which files the user opened, modified or deleted at the certain time period
- Establishing the usage of removable media and data transfer from/to removable media
The insights into the subject’s computer usage that an investigator can collect can be extremely valuable for many types of investigations. It should be noted, KeyScout usage is not limited only to OS system files collection. The utility recovers both user data and a vast variety of credentials that can be used for immediate cloud data extraction in Oxygen Forensic Cloud Extractor.