Android Agent is an application that allows the extraction of data from any unlocked Android device.
Android Agent is used to acquire user data and media files when physical or full file system extraction is not available. However, it can also be used for fast and selective data extractions when only certain artifacts need to be acquired.
We introduced the Agent extraction method in 2004 and have added many improvements since then. Let’s have a look at all the functions of the latest Android Agent:
- Logical data extraction
- Manual data collection
Logical data extraction
Logical data extraction via Android Agent can be performed on any unlocked device running Android OS 4-14 via USB or Wi-Fi.
To perform it, open Oxygen Forensic® Device Extractor from the Oxygen Forensic® Detective Home screen and choose “Android Agent extraction”. Read the instructions and then choose either extraction via USB over Wi-Fi and proceed with the extraction.
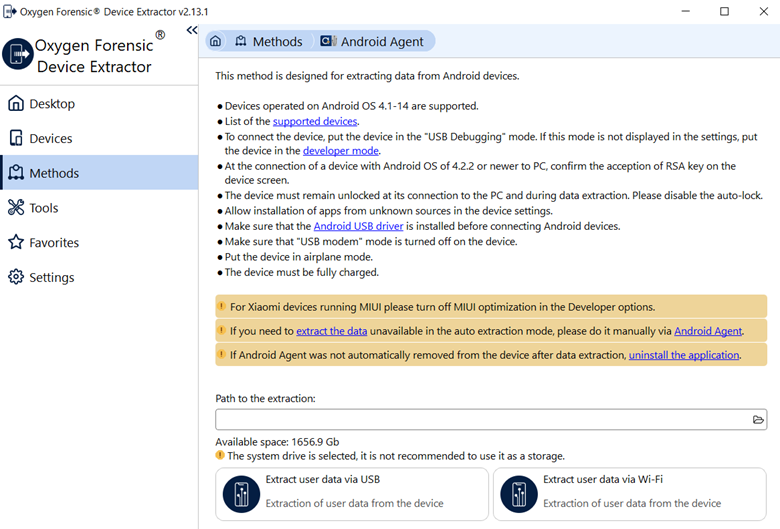
No matter which is chosen, USB or Wi-Fi, you can expect the extraction of following evidence:
- calendars
- calls
- messages
- owner profile
- contacts
- Wi-Fi access points
- Bluetooth-paired devices
- file structure
- app data from the external memory
Once data is extracted, you will be given the option to open it in Oxygen Forensic® Detective for analysis. Neither applications nor files from the internal memory will be extracted via Android Agent because it has no rights to access the internal folders.
To extract apps and files, use the physical and full file system extraction method for Android devices.
Manual data extraction
Manual data extraction can be used in several cases:
- Damaged USB Port or WiFi security protocols that do not allow connection
- Collection of applications that are not supported by Android Agent via USB or Wi-Fi
- Screenshots or screen recordings of device data
For all cases, Android Agent will need to be installed on the device. Use an OTG device or SD card to copy Android Agent to a device, install it, and run it. Several options will appear on the Android Agent welcome screen:

- Extraction of internal and external storage. Android Agent will collect all the data from the folders to which it has access. Extraction will be identical to the extractions performed via USB or Wi-Fi. The only difference is that you select all the options within the running app on the target device, not in Oxygen Forensic®Device Extractor.
- Screenshots and screen recordings. Using this option, you can take screenshots or screen record any data. Screenshots can be done in manual or semi-automated mode.
- Third-party application data. Use this option to manually collect data from WhatsApp, WhatsApp Business, Signal, Discord, Twitter, Line, Kik, AWS Wickr, Opera, Chrome, Firefox and other supported apps.

Select an app, read the instructions, and choose the app artifacts for extraction.

- Data via Wi-Fi. Use this option to extract data using a Wi-Fi connection. Android Agent will display the IP address that needs to be entered into Oxygen Forensic®Device Extractor.
A destination folder is necessary no matter what data is manually collected. Once data is collected, investigators can import it in Oxygen Forensic® Detective, choosing the “Agent extraction” option on the Home screen.