
Despite MediaTek and Qualcomm being industry leaders when it comes to chipsets, more and more smartphones are operating on UNISOC nowadays. With Oxygen Forensic® Detective v.16.0, investigators are now able to extract hardware keys and decrypt physical dumps of devices based on the UNISOC T606, T616, T612, and T310 chipsets and running Android OS 10 – 13.
What is UNISOC?
UNISOC is a Chinese company that was previously known as Spreadtrum. Founded in 2001, it originally produced chips for entry-level cell phones. This policy proved to be successful: in 2008 the majority of China Mobile subscribers were using phones built on Spreadtrum processors. This turned Spreadtrum into a telecommunications giant.
The company entered the global market in 2012, when its chipsets were used in ultra-budget 2G smartphones from Lenovo and Samsung. For a period of time the company was unable to readjust to the booming smartphone market, and gradually its market share slipped below 3%.
Everything changed in 2017 when Intel showed interest in Spreadtrum. One year later, Intel invested 1.5 billion in exchange for 20% of the company’s shares. Since then, the performance of the brand’s chipsets grew rapidly. In 2019, thanks to development investments from Intel, the company which name had been changed to UNISOC, introduced new chips called Tiger. By the end of 2021, the company would take 11% of the market share, overtaking Samsung Exynos and HiSillicon Kirin (Huawei).
Although UNISOC is still a long way from market leadership, in the last few years it has firmly established itself as a major player in 4th place behind MediaTek, Qualcomm, and Apple.
UNISOC support in Oxygen Forensic® Detective
Understanding this growth, Oxygen Forensic® Detective includes a data extraction approach for Android devices that operate on UNISOC chipsets. The extraction method is based on exploiting a vulnerability in the low-level proprietary protocol that enables gaining access to data from password-locked devices.
Oxygen Forensic® Detective currently supports data extraction from devices based on UNISOC T610, T618, T700, T606, T616, T612, and T310 chipsets.
Potential Hurdles
User data encryption
User data encryption is enabled in all modern Android devices by default and cannot be disabled. Starting with Android 10, the file-based encryption (FBE) is used on the devices, implemented with the aid of hardware keys.
The memory of all modern UNISOC-based devices is encrypted. The hardware key, knowledge of the screen lock password, and the encryption mechanism are required for successful data decryption.
One part of the encryption algorithm is the same for all Android devices, while the other part is implemented in the Trusted Execution Environment (TEE) and depends on the TEE OS. The vast majority of UNISOC devices use Trusty TEE. This uniformity allows for implementing support of the extensive list of devices from different vendors.
In the event that the device is using file-based encryption, there are two data storage options:
- Device Encrypted (DE)
- Credential Encrypted (CE)
Data from DE storage is encrypted solely with the use of the hardware key and is accessible before password entry. Data from CE storage is encrypted using both the screen lock password and hardware key. If the screen lock password is not set, data from both storages gets encrypted in the same way.
In order to decrypt all user data, an investigator must enter or brute force the screen lock password of the device under investigation. It is also possible to import the image without password entry. However, in this case, data from the CE storage won’t be available.
Oxygen Forensic® Detective allows brute forcing the screen lock password. The speed depends on the PC from which the investigation is conducted. The GPU memory size is what affects the speed the most.
Since most users have a PIN of 4-6 digits or a pattern set as a lock screen password, the brute force process completes relatively fast. There are only about 1.5 million possible combinations, and it takes less than an hour to obtain the right passcode even when using a simple PC with an integrated GPU. On a PC with RTX 3080 Ti, the same process will take less than 3 minutes.
Solution
Extraction of hardware keys
A vulnerability in the low-level proprietary protocol is exploited for the extraction of hardware keys. A special mode SPRD COM port serves as an entry point. In order to utilize it, connect a powered off device via USB by holding the volume up or down button, depending on the device.
The vulnerability is contained in the BootROM and cannot be fixed with a software update. Once the vulnerability is exploited, it is possible to execute an arbitrary code with EL3 privileges on the device, which is enough to extract hardware keys from it. All actions are performed in RAM (Random Access Memory) and once the device is rebooted or the battery is re-inserted, the device returns to its original state. This means that the approach is non-destructive and safe for the data and the device.
Please note that UNISOC-based Samsung devices are not currently supported in Oxygen Forensic® Detective, but we are working on a solution. The main complication when enabling data extraction from UNISOC-based Samsung devices and its decryption is that the OS structure of Samsung devices differs from the standard one, i.e. the ODIN protocol is added and some parts of the SPRD protocol are cut out. Besides, putting a Samsung device in SPRD COM-port mode involves short-circuiting the test point on the device board.
How-to Extract Data from UNISOC-based Devices
Guide to the data extraction process:
Select the correct model of the device that you will extract data from.
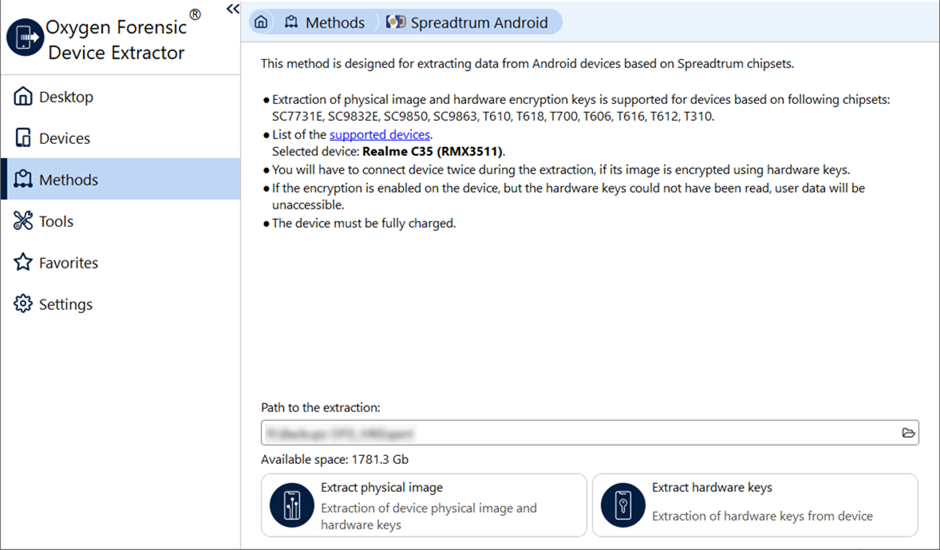
Connect the device in the SPRD COM-port mode. In most cases, this means connecting a powered off device via USB.
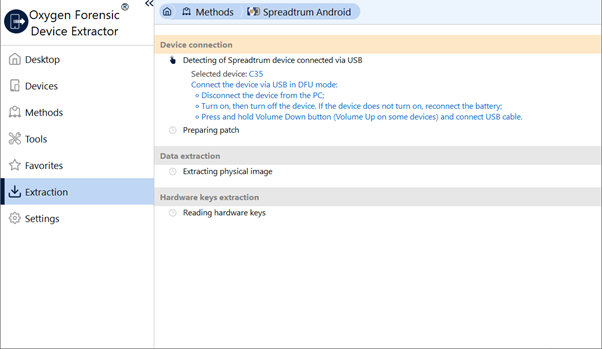
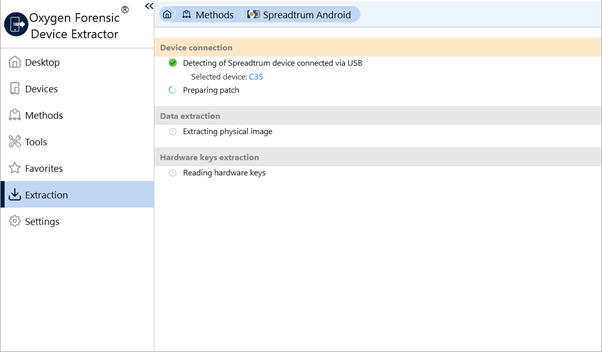
Wait while the BootROM vulnerability is being exploited.
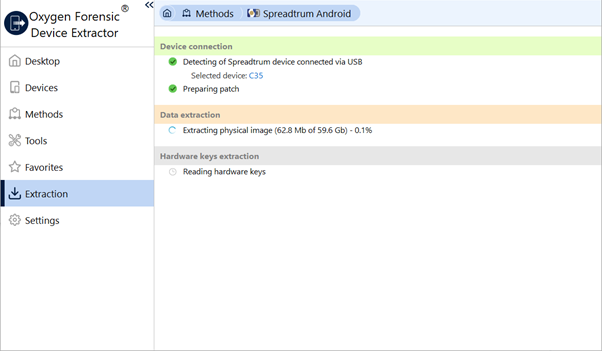
Extraction of the physical image.
Extraction of the hardware keys.
Steps in the importing process:
- Enter screen lock password or initiate the brute-force of it.
- The software generates the key that will be used for the decryption of user data.
- The decryption of the user data.