
Oxygen Forensics has been offering passcode brute force for mobile devices for many years. With this module you can decrypt data of Android devices based on MTK, Qualcomm, UNISOC, and Exynos chipsets as well as various types of device backups including iTunes.
The time has come to introduce our new brute force module – Oxygen Forensic® KeyDiver. It is available within Oxygen Forensic® Detective at no additional charge. The module is designed to find passwords to decrypt:
- partitions protected with BitLocker
- partitions protected with FileVault 2
- encrypted ZIP files
- encrypted Apple Notes
- passcode-locked Telegram Desktop app
Our list of supported partitions, files, and applications continues to grow.
With Oxygen Forensic® KeyDiver, you can:
- create hash-cracking attacks in a format supported by the Hashcat utility using various dictionaries and masks
- run sequential attacks until the password is successfully guessed
- export the obtained password to decrypt the original data or use it for other purposes
How to use Oxygen Forensic® KeyDiver
1.Creating an attack
The module is based on the Hashcat tool, which is known as one of the best open-source solutions that supports hundreds of hash types.
You can use hashes obtained from the third-party sources or use the attack settings file (.json) obtained from Oxygen Forensic® Detective.
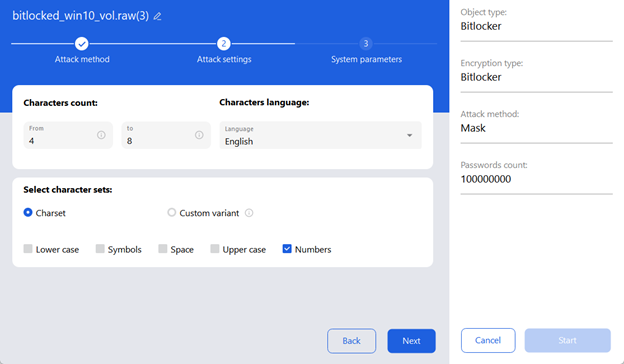
After entering the hash in the input field, the user should specify the attack method: a mask attack or a dictionary attack.
A mask attack tries to guess the target password by systematically testing all the possible combinations of specified characters that match a specific pattern. For example, it can be “All digits, 4 to 8 characters long,” and then all the combinations of digits from 4 to 8 characters will be generated and tested.
A dictionary attack uses a dictionary file that contains a pre-selected list of passwords arranged one per line. Each password from the file is tested sequentially.
2. System settings
The last step before running an attack is to determine what hardware will be used for the attack, as well as the maximum allowable temperature and load on it.
As shown in the screenshot below, the user can select one of the four efficiency modes, set the temperature threshold to stop the attack, and choose one or more video cards.
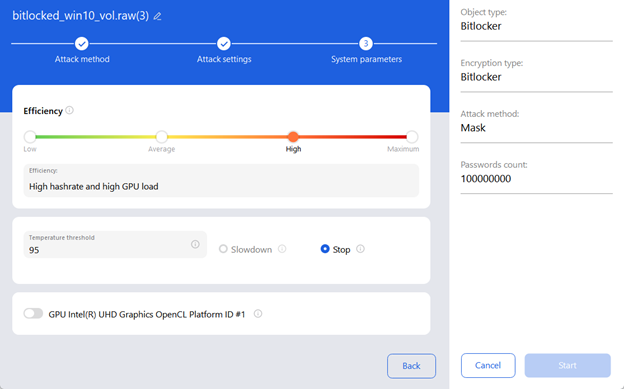
Efficiency determines how much the GPU is involved in the attack. Maximum efficiency provides the best hash rate and maximizes hardware utilization, but it can also lead to significantly higher operating temperatures and high power consumption.
Oxygen Forensic® KeyDiver monitors the GPU temperature. If the appropriate sensors are available on the device, the module
To run an attack, the user should select at least one GPU. If multiple GPUs are selected, they will be used simultaneously, which will significantly boost the attack speed. If the GPUs are incompatible, a corresponding notification will be displayed.
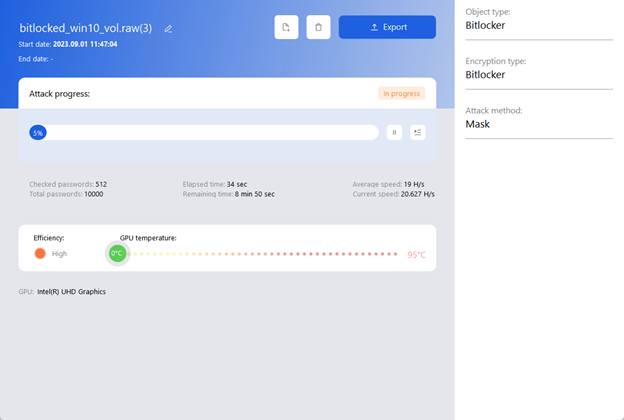
3. Running attacks
Once both the attack settings and at least one GPU are selected, you can run the attack by clicking the “Start” button.
Only one attack at a time can have the “In progress” status in the current module version.
You can add the current or new attack to the queue and they will be processed automatically. The next attack will start as soon as the previous one finishes.
Once the attack starts, it is possible to monitor the details of its progress in a separate window.
The “Attack manager” window allows you to view all ongoing, finished, paused, and queued attacks, manage them, and sort them by various parameters.
Attacks can be managed straight from the list via the context menu, which can be opened by clicking the three dots on the right side of each attack line.
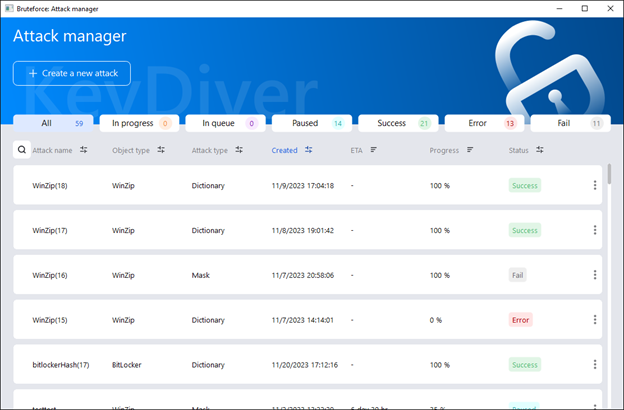
If the password was not guessed successfully, the suggested next step could be to launch a new attack on the same hash but with adjusted settings: for example, using another dictionary. Oxygen Forensic® KeyDiver enables you to utilize any existing attack as a template for a new attack.
In the case of a successful attack, the password will be displayed in the corresponding field. It can then be copied by clicking the corresponding icon in the “Password” field. It is also possible to save the password on the current device in .txt format (using the “Save” button) or export the attack results in .json format (using the “Export” button).
For more detailed instructions on this utility, please refer to the Oxygen Forensic® KeyDiver User Guide included in the Oxygen Forensic® Detective installation package.