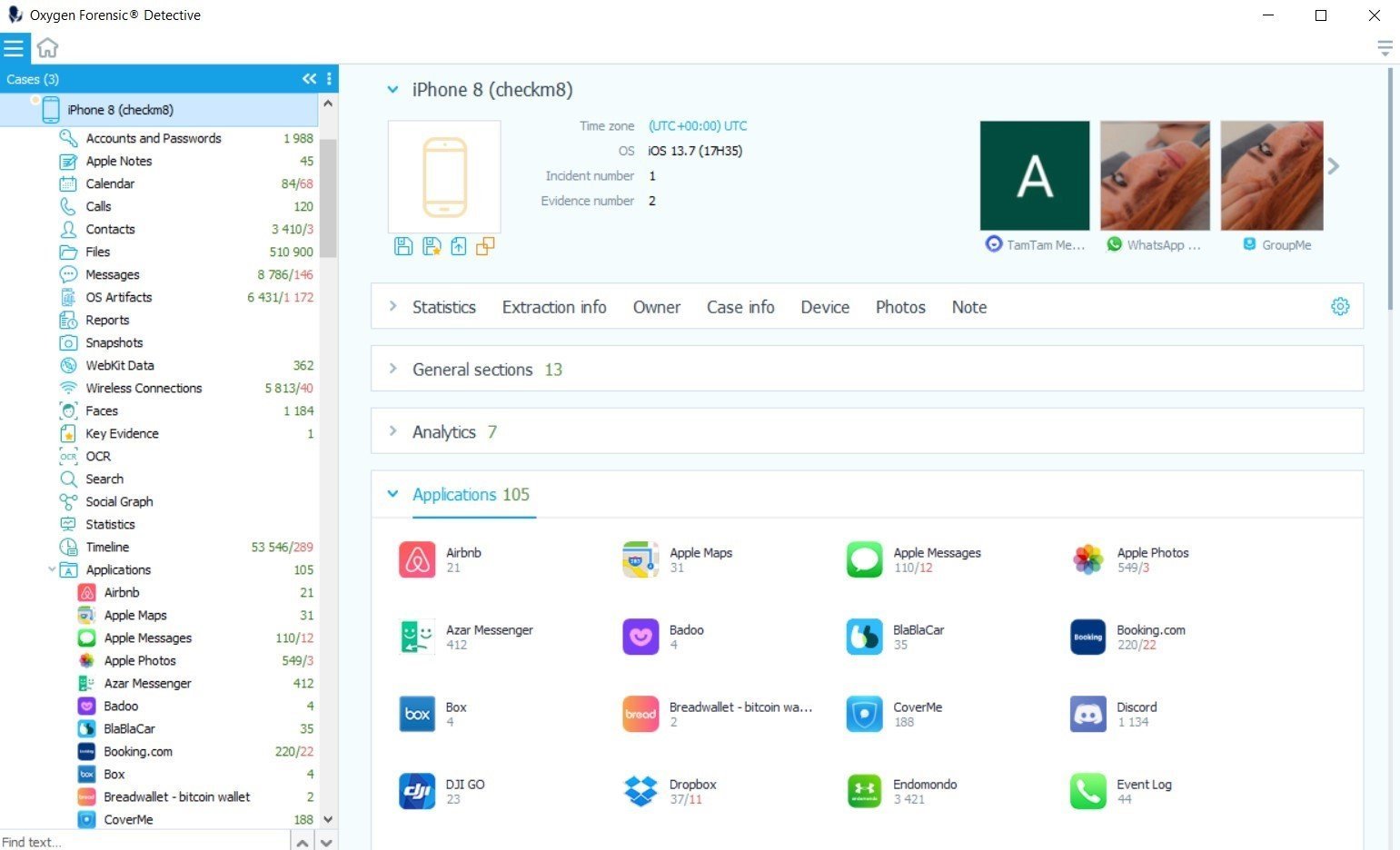
With items like the iPhone, iPad, and iMac in their product line, Apple Inc. needs no introduction. Their popularity in the mobile device industry has led us to place high importance on developing solutions that support the latest iPhones and iPads.
Today, our all-in-one forensic solution, Oxygen Forensic® Detective, can extract, decrypt, and analyze data from all existing models of iPhone and iPad. Additionally, we offer multiple avenues for acquiring and recovering data, with each method giving the investigator access to a slightly different dataset. In this article, we will focus on iPhones and the support provided by Oxygen Forensic® Detective. Let’s start by reviewing our supported devices.
Supported Devices
Overall, Oxygen Forensic® Detective’s support expands through the entirety of the iPhone product line. However, the extraction methods that allow our software to extract data from each device are different.
As previously mentioned, there are several alternative extraction methods included in our software. Some of these extraction methods can acquire vastly comprehensive datasets of existing and deleted data, others offer more limited extractions. The following section will cover each extraction method along with their supported devices.
Extraction Methods
1) Full File System Extraction
a) Checkm8 – Automatic extraction of supported devices that include Apple’s A7 to A11 SoC, from iPhone 5s through X running up to iOS 14.7 beta.
b) Checkra1n and Unc0ver – Extraction of jailbroken devices that include Apple’s A7 to A11 SoC.
2) iTunes Logical Extraction – Supported Apple iOS versions are 8.0 – 14.7 beta.
3) Logical File Structure Extraction – Files available via PTP protocol can be extracted. Supported Apple iOS versions are 8.0-14.7 beta.
Data Access
Datasets will vary depending on the extraction method and whether the device is unlocked or not. Currently, Oxygen Forensic® Detective allows investigators to extract the following data:
Full File System Extraction via Checkm8
If the password is known, all data can be recovered. This includes all device and system files, applications, as well as the complete keychain. Extract data from over 22,000 supported apps, including secure apps like Signal, Wickr Me, ChatSecure, Snapchat, Facebook Secret Chats. Investigators will have full access to the keychain and encryption keys from secure apps, as well as all available deleted records.
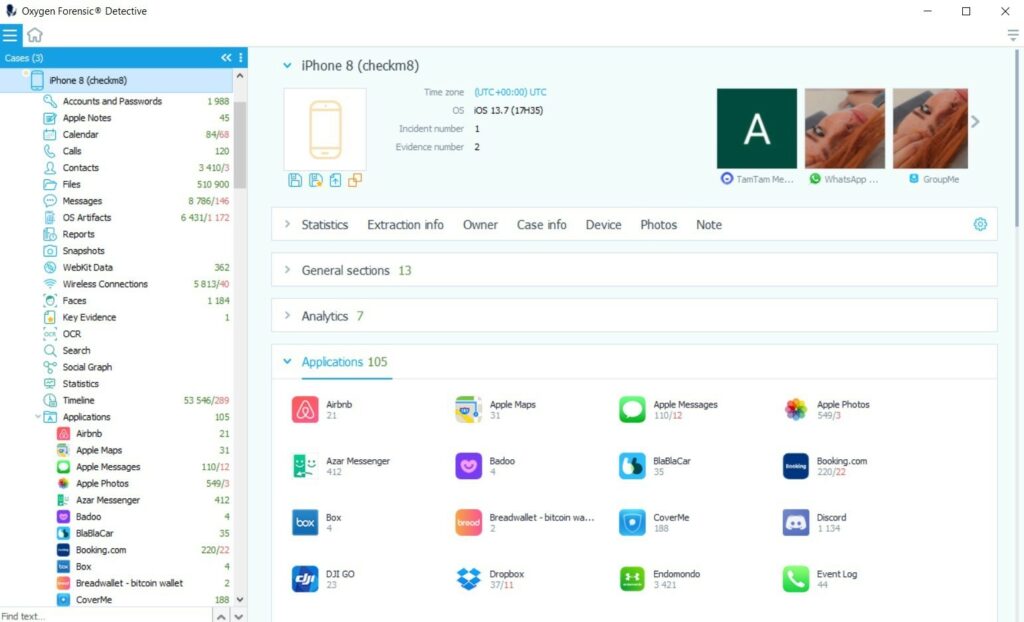
If the device is locked and the password is unknown, investigators will be able to extract limited data and only some parts of the keychain using the BFU (Before First Unlock) method.
Learn more about the checkm8 method in our previous blog post.
Full File System Extraction of Jailbroken devices
Extract full file systems and keychains from devices already jailbroken with Checkra1n, Unc0ver, and other available jailbreaks.
iTunes Logical Extraction
Access user accounts and passwords, call records, contacts, messages, browser history, Wi-Fi connections, third-party emails, maps, photos, videos, calendar info, and identified faces. Deleted data will not be available due to method restrictions.
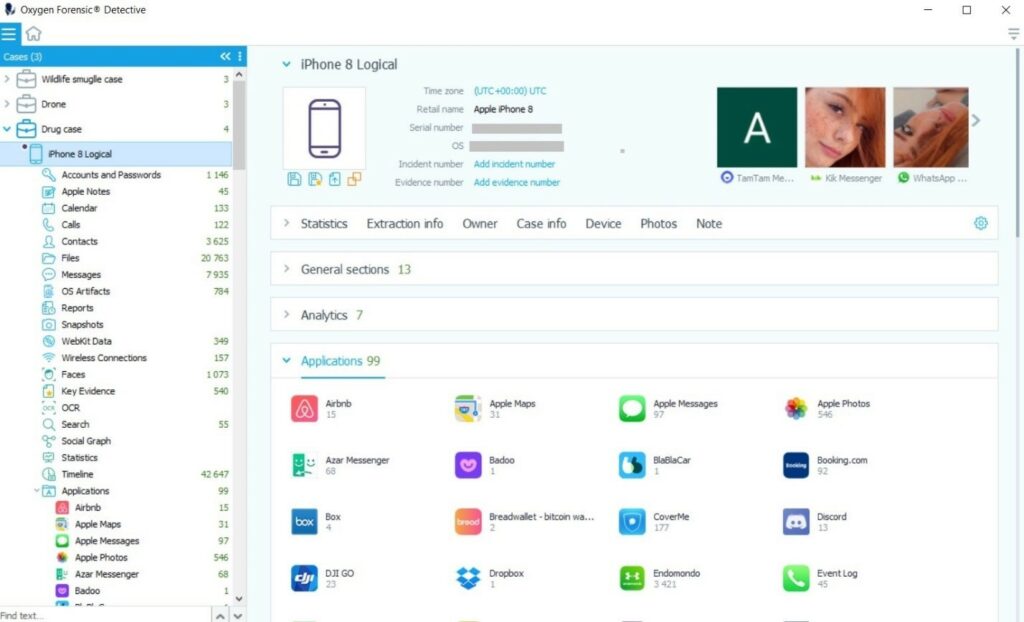
Logical File Structure Extraction
Access the DCIM folder or files available via the Picture Transfer Protocol.
Analyzing the Data
In addition to Oxygen Forensic® Detective’s comprehensive extraction and parsing capabilities, the software provides an analytics section built directly into the platform. There, investigators can access a full suite of powerful, industry-leading analytic tools including features like Facial Categorization, Optical Character Recognition, Selective Extraction, Social Graph, Timeline and more.