
Today’s users are demanding more and more secure applications. This need by users is really a catch22 as an investigator. What is great as a user to have access to a wide variety of secure messengers to safely communicate, law enforcement and corporate investigators find encrypted applications one of the biggest challenges when they need to access digital evidence.
We have placed great importance on researching secure applications. Oxygen Forensic® Detective currently supports a wide range of encrypted apps to include Signal, Wickr Me, Threema, CoverMe, Snapchat, and others.
With the release of Oxygen Forensic® Detective 13.1, the Wire app was added to the cadre of supported encrypted apps. Wire is one of the most comprehensive collaboration suites, featuring a messenger that allows for text, voice, video, conference calls, file-sharing – all protected by secure end-to-end-encryption.
Besides security, Wire helps users keep their anonymity by allowing them to register by email and will not expose their phone number to other Wire users. If a user does not give Wire access to their contacts and number, shared contacts will not receive a notification that the contact has a Wire account as well.
Let’s see how Wire app data can be extracted from mobile devices using Oxygen Forensic® Detective.
Apple iOS devices
Support for the Wire app is covered under the Apple iOS full file system extraction. Valuable data is extracted using this full filesystem extraction method via our built-in checkm8 workflow as well as by connecting an Apple iOS devices that has, or is, already jailbroken, including the latest checkra1n and unc0ver exploits. In either case, the investigator simply selects the “iOS Advanced extraction” option in Oxygen Forensic® Extractor.
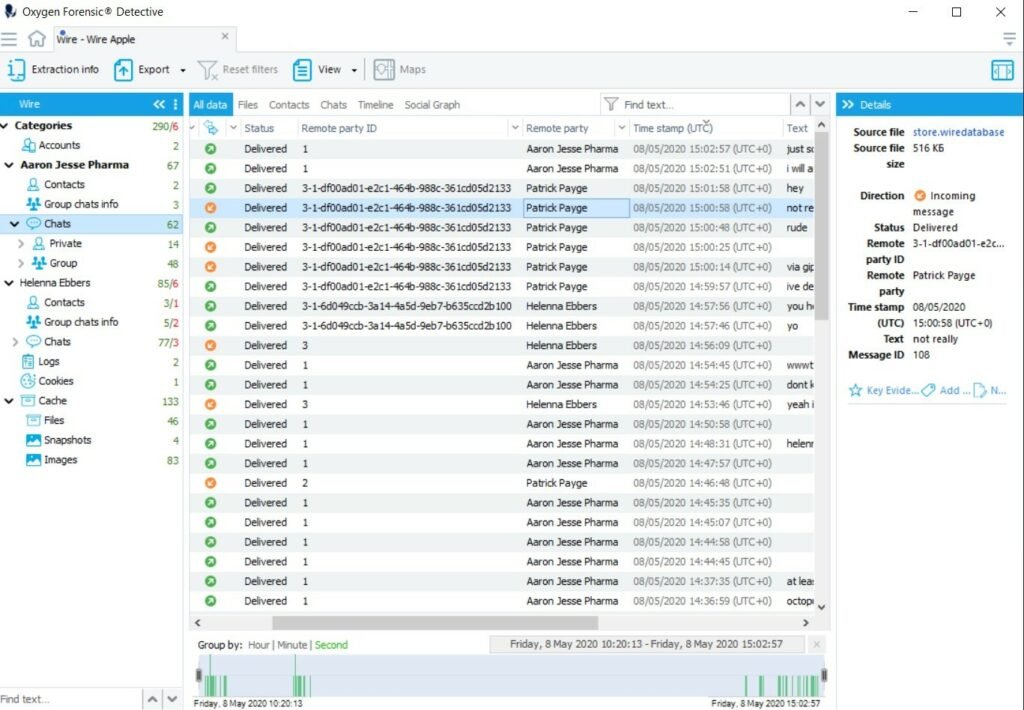
The evidence set will include:
- Account details
- Contacts
- Group and private chats
- Logs
- Cookies
- Cache
If several Wire accounts are used on a device, all can be extracted. This feature works for both Apple iOS and Android devices.
Android devices
Physical data extraction is required to access the Wire app on Android devices. Investigators can use any supported screen lock bypass method (for Kirin, Exynos, Qualcomm, MTK, and Spreadtrum chipsets). They can also extract an Android device where root rights can be obtained and subsequently collected using Oxygen Forensic® Extractor.
The evidence set will include:
- Account details
- Wire and Phonebook contacts
- Information about the devices where the Wire account had been used
- Group and private chats
- Group and private calls
- Files
- Downloads
- Cache

To try this functionality in Forensic® Detective, ask for a fully-featured demo license here.