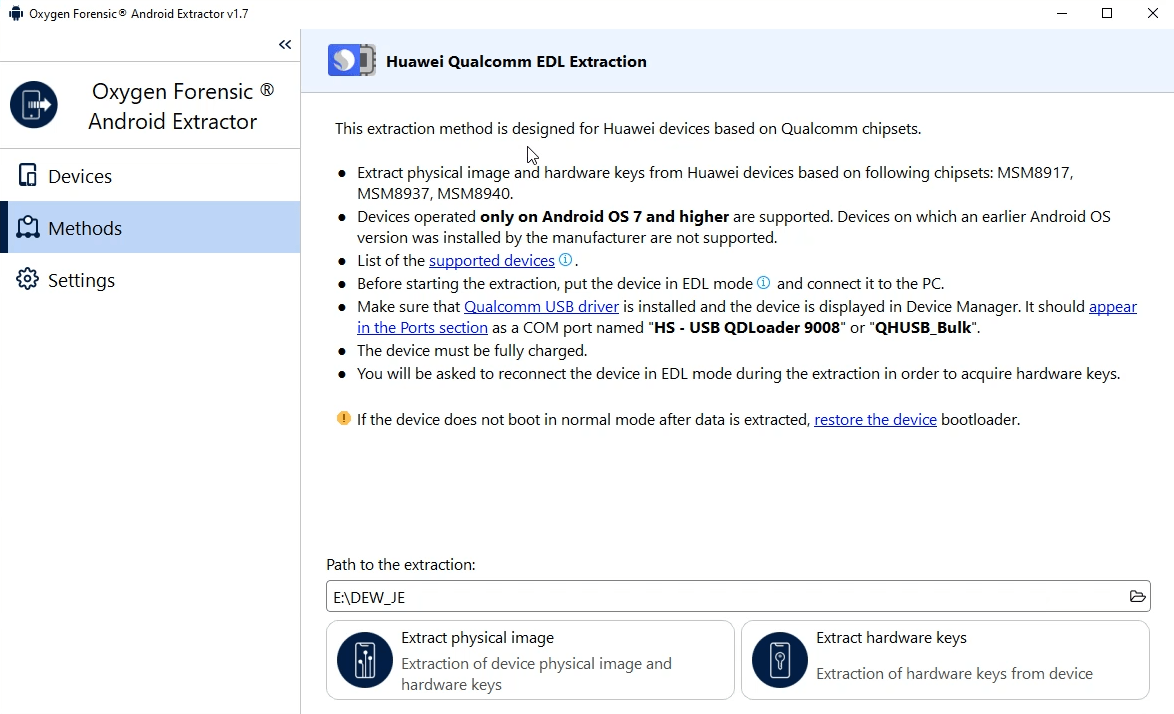
Huawei devices have always been considered to be one of the most secure due to the extra layer of security. Last year, we were the first in the industry to offer screen lock bypass and physical extraction capabilities for the latest Huawei devices based on Kirin chipsets and running Android 9-10 without having to send for premium services. In Oxygen Forensic® Detective v.13.6, we have made yet another step forward, providing law enforcement with a new advanced method of evidence extraction and decryption from Huawei devices based on Qualcomm chipsets. This method works with Huawei devices running Android OS 7 or higher and using File-Based Encryption (FBE). The following Qualcomm chipsets are supported: MSM8917, MSM8937, and MSM8940. The method covers over 50 devices, including Huawei Honor 6A, Huawei Honor 7A, Huawei Y6, Huawei Y7, Huawei Enjoy 8e, Huawei Mediapad T3 10, Huawei Mediapad M3 Lite 8, etc.
How is this done in OFD?
- Select the “Huawei Qualcomm Android dump” method in the Oxygen Forensic® Extractor and read the initial instructions carefully. Make sure the device is fully charged and that Qualcomm drivers are installed. Next, put the device in EDL mode, removing the device back panel and shorting the test point contacts.
2. Once the device is in EDL mode, connect it to the PC running OFD and wait for the extraction to start.
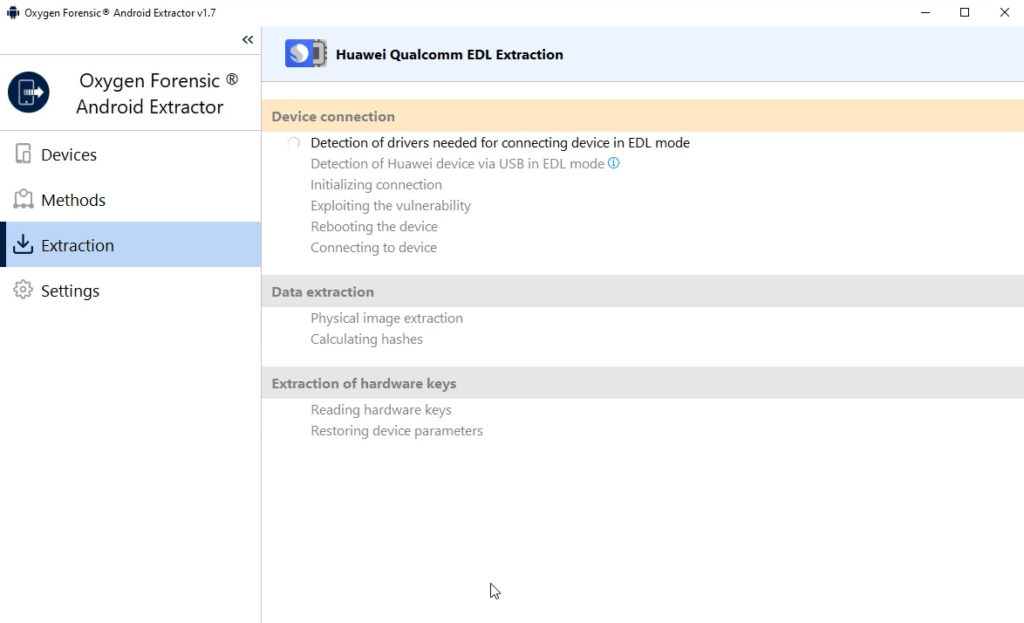
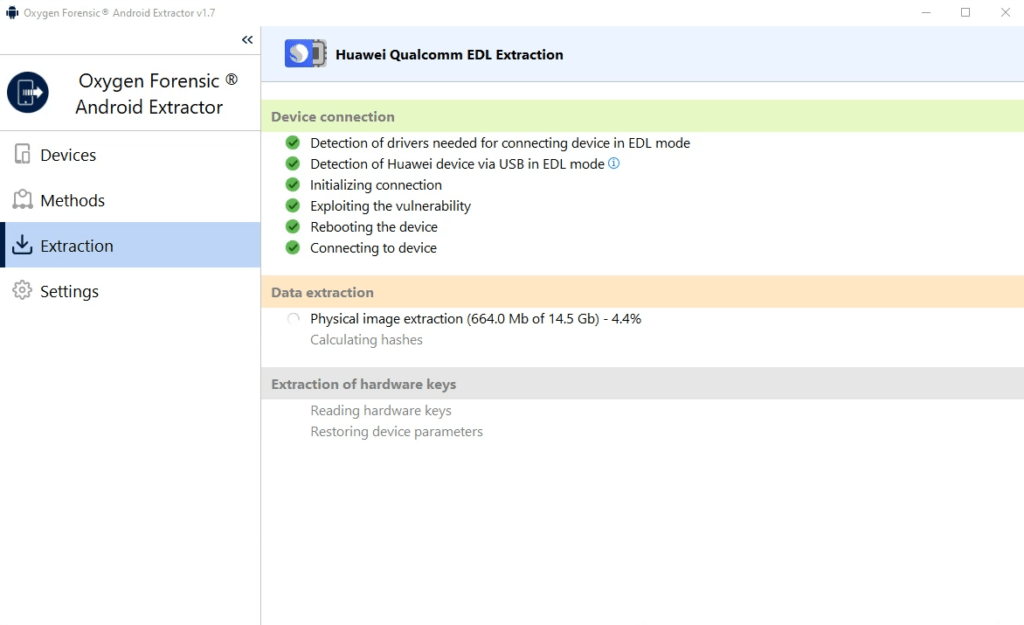
3. Once the extraction is complete, the software will also extract the hardware keys required for decryption. Because the user passcode is not used to decrypt Qualcomm-based Huawei devices, brute force is not required.
4. The final step is to open the extracted dump in Oxygen Forensic® Detective for analysis.
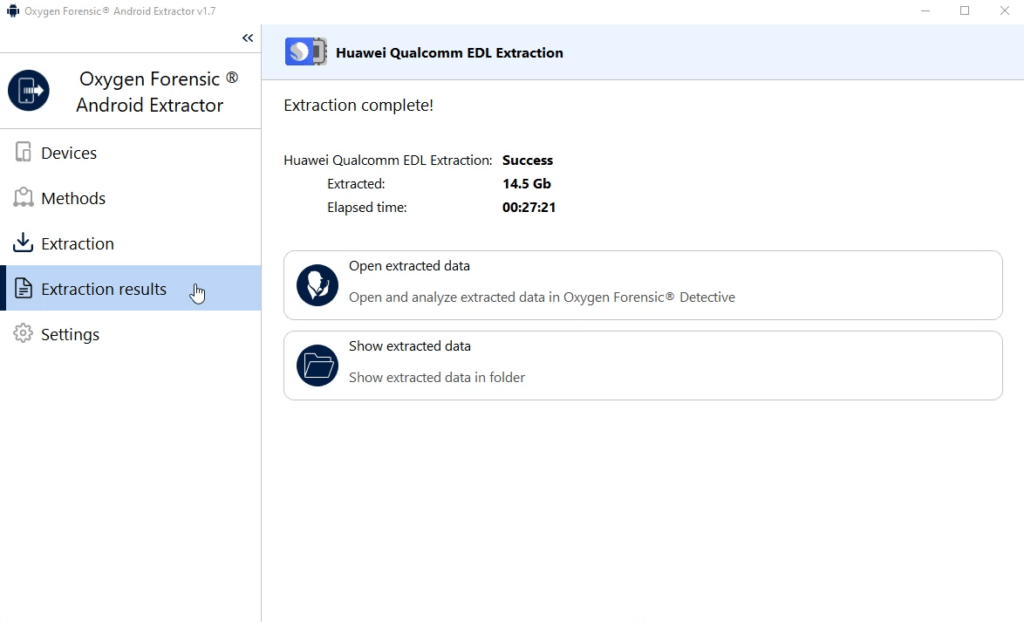
If the device does not boot into normal mode after the extraction, return to the initial window of the “Huawei Qualcomm EDL Extraction” method and use the available link to restore the device.
Besides the screen lock bypass methods for Huawei devices, Oxygen Forensic® Detective offers data extraction from Huawei cloud and parsing of HiSuite backups. Learn more in our previous article.
For step-by-step instructions on how to extract and decrypt evidence from Huawei devices based on Kirin chipsets, watch our video.