Table of Contents
Digital forensics, also known as computer or mobile forensics, deals with investigating and recovering digital evidence from electronic devices and networks. It involves applying scientific and investigative techniques to gather and analyze data that could be used in a criminal case or legal proceedings.
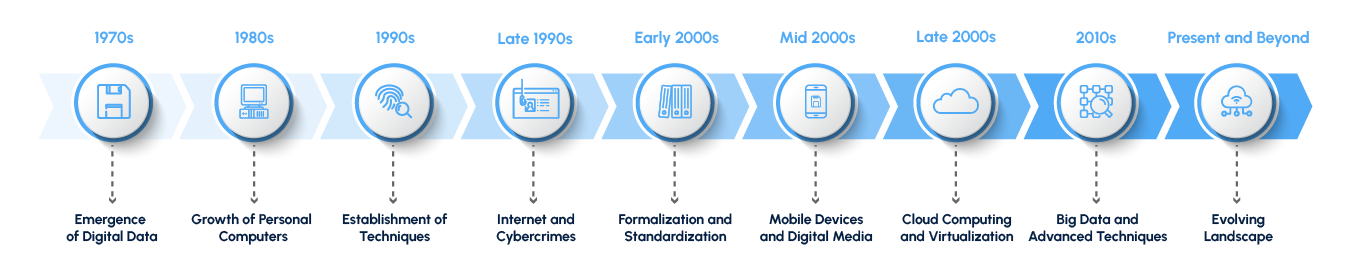
Digital forensics is a field that continues to evolve to keep up with the pace of technological advancements. So when and how did it start?
- 1970s – Emergence of Digital Data: The earliest forms of digital forensics can be traced back to the 1970s, when digital data started becoming more prevalent. Computers were primarily mainframes and minicomputers at this time.
- 1980s – Growth of Personal Computers: With the rise of personal computers in the 1980s, there was an increased need for methods to investigate computer-related crimes. Early digital forensics efforts focused on analyzing computer systems to recover evidence.
- 1990s – Establishment of Techniques: The 1990s saw the establishment of foundational techniques and tools for digital forensics. Law enforcement agencies and cybersecurity experts began developing protocols and methodologies for investigating digital crimes.
- Late 1990s – Internet and Cybercrimes: As the internet became more accessible and widespread, cybercrimes emerged as a major concern. Digital forensics had to adapt to the challenges posed by crimes committed online, such as hacking, identity theft, and online fraud.
- Early 2000s – Formalization and Standardization: The early 2000s brought about greater formalization and standardization of digital forensics processes. Organizations like the International Association of Computer Investigative Specialists (IACIS) and the National Institute of Standards and Technology (NIST) started providing guidelines and best practices for digital investigations.
- Mid 2000s – Mobile Devices and Digital Media: The increase of mobile devices and digital media storage expanded the scope of digital forensics. Analysts had to develop techniques for extracting evidence from a variety of devices, including cell phones, USB drives, and memory cards.
- Late 2000s – Cloud Computing and Virtualization: The advent of cloud computing and virtualization presented new challenges for digital forensics. Investigators had to adapt to the decentralized nature of data storage and the complexities of virtual environments.
- 2010s – Big Data and Advanced Techniques: The explosion of big data and the use of advanced technologies like machine learning and artificial intelligence started influencing digital forensics. These technologies allowed for more efficient analysis of large volumes of data to uncover patterns and insights.
- Present and Beyond – Evolving Landscape: Digital forensics continues to evolve as technology advances. The increasing use of encryption, the Internet of Things (IoT), blockchain, and other emerging technologies presents both new opportunities and challenges for digital investigators.
Throughout its history, digital forensics has become an integral part of law enforcement, cybersecurity, and legal proceedings. Its creation and growth has benefited the community at large.
Types of Digital Forensics
Digital forensics encompasses various specialized fields, each focused on a specific aspect of digital investigation.
Here are some of the main types of digital forensics:
- Computer Forensics
- Mobile Device Forensics
- Cloud Forensics
- Network Forensics
- Memory Forensics
- Digital Media Forensics
- Forensics Data Analysis
- Database Forensics
- Malware Analysis
- IoT (Internet of Things) Forensics
Computer Forensics
This is the most well-known type of digital forensics. It involves the investigation of computers, laptops, servers, and other computing devices to recover evidence related to crimes or incidents. This could include analyzing file systems, deleted files, metadata, and logs to determine what actions were taken on the system.
Mobile Device Forensics
Mobile forensics deals with extracting and analyzing data from mobile phones, tablets, and other portable devices. Investigators may recover text messages, call logs, emails, GPS data, and app usage information to reconstruct a user’s activities.
Learn more about Mobile Forensics – types, history, and challenges →
Cloud Forensics
As more data moves to cloud-based environments, cloud forensics has emerged. Investigators analyze cloud storage and services to determine if they’ve been used for illegal activities or to locate potential evidence.
Network Forensics
This type involves monitoring and analyzing network traffic to identify and investigate security breaches, unauthorized access, or suspicious activities. Network forensics can help reconstruct the timeline of events during a cyber attack.
Memory Forensics
Memory forensics involves analyzing a computer’s volatile memory (RAM) to gather information such as running processes, open network connections, and encryption keys. This can be crucial in understanding an attacker’s actions.
Digital Media Forensics
Digital media forensics focuses on the analysis of multimedia files, such as images, audio recordings, and videos. Investigators examine these files for signs of manipulation or tampering to determine their authenticity.
Forensics Data Analysis
This type involves using data analysis techniques to uncover patterns, trends, and anomalies within large volumes of digital data. It can help investigators identify relationships between entities and understand the context of an incident.
Database Forensics
Database forensics involves the analysis of databases to uncover unauthorized access, data tampering, or other illicit activities. It’s commonly used in cases involving data breaches and corporate espionage.
Malware Analysis
In this field, analysts dissect and study malicious software (malware) to understand its behavior, purpose, and potential impact. Malware analysis helps in identifying the tactics used by cybercriminals and in developing countermeasures.
IoT (Internet of Things) Forensics
With the growth of IoT devices, this field focuses on investigating smart devices, wearables, and other IoT technologies for digital evidence in cases related to privacy breaches or cybercrimes.
These different types of digital forensics all contribute to the broader field of digital investigation, enabling to uncover evidence, track down cybercriminals, provide insights for legal proceedings, and much more.
Use Cases.
Digital forensics has a wide range of use cases across various industries and contexts.
Here are some notable examples:
- Criminal Investigations: Law enforcement agencies use digital forensics to investigate cybercrimes, fraud, hacking, and other digital offenses. They analyze digital evidence such as emails, text messages, internet history, and metadata to trace the activities and movements of suspects.
- Incident Response: Organizations employ digital forensics during and after cybersecurity incidents to determine the cause, extent, and impact of breaches or attacks. This helps them identify vulnerabilities, prevent further attacks, and improve their security posture.
- Data Breach Analysis: Digital forensics specialists analyze compromised systems, databases, and network logs to understand how a data breach occurred, what data was accessed or stolen, and who might be responsible.
- Intellectual Property Theft: Companies can use digital forensics to investigate cases of intellectual property theft, such as trade secret leakage, patent infringement, and copyright violations.
- Fraud Detection: Forensic analysts examine financial records, digital transactions, and communication logs to identify patterns indicative of fraud or financial misconduct.
- Litigation Support: Digital evidence can be crucial in legal cases involving intellectual property disputes, contract breaches, defamation, and more. Digital forensics experts help uncover, preserve, and present evidence in a legally admissible format.
- Employee Misconduct: Organizations may use digital forensics to investigate cases of insider threats, harassment, and inappropriate use of company resources by employees.
- Child Exploitation Cases: Law enforcement agencies combat child exploitation by using digital forensics to uncover evidence of illegal images, videos, or communications on suspects’ devices.
- Counterterrorism Efforts: Governments and security agencies use digital forensics to track online communications, financial transactions, and social media activities of individuals and groups involved in terrorist activities.
- Malware Analysis: Security professionals use digital forensics to reverse-engineer malware and understand its behavior, origin, and potential impact on systems.
Digital Forensic Tools.
Oxygen Forensics specializes in digital forensic software solutions. It provides tools and software for law enforcement, private investigators, enterprises, and government organizations to extract, analyze, and recover digital evidence from various devices, including mobile phones, computers, cloud services, and more.
Oxygen Forensics offers a range of products and services that are crucial in criminal and legal investigations, corporate incidents, and other situations where digital evidence plays a role.
10 questions to ask before purchasing Digital Forensic software →
Oxygen Forensic® Detective
Oxygen Forensics’ flagship solution, Oxygen Forensic® Detective, was built to support investigators throughout the entire investigative process. It can extract data quickly and completely from the full digital landscape and facilitate deep analysis and flexible reporting in a single platform. It extracts data and artifacts from various sources with the capability for mobile, cloud, and computer forensic investigations.
Oxygen Analytic Center
Oxygen Analytic Center, built to support Oxygen Forensic® Detective and Oxygen Corporate Explorer, as well as an individual product, enables real-time, browser-based collaborative data review and analysis — any ti
me, anywhere — so investigators and eDiscovery professionals can resolve cases faster and more efficiently.
Oxygen Corporate Explorer
Oxygen Corporate Explorer, built for corporate investigations, helps find critical digital evidence quickly and completely, using targeted, remote and onsite data collection, task scheduling for automatic collection, and powerful search and analytic tools.